This Blog will be about the basics of troubleshooting Windows updates for business (WUfB) and the specific case we had where GPO policies were not cleaned by the imaging process or EseUtil. After finding the issue we are going to resolve it with a remediation script.
Failing to install Windows Updates case
So let’s first go into the case where the customer was having issues getting the latest Windows Updates, they had had a new device enrollment with Windows 11 somewhere in the same year. After a while, WufB reporting showed the devices were missing security updates. Only after trying to update it manually, for our first ring users we were able to update Windows without any issues. Now the first troubleshooting actions needed to be done.
Troubleshooting
Windows Update for Business (WUfB) is a service that allows you to manage and deploy Windows updates to your devices using the cloud. WUfB offers many benefits, such as reducing the need for on-premises infrastructure, simplifying update management, and providing more control over the update experience.
Check if Windows Updates is checked in Graph
If we log on to Graph Explorer we can see the device enrollment state, first go to Graph Explorer | Try Microsoft Graph APIs – Microsoft Graph, here we need to use the https://graph.microsoft.com/beta/admin/windows/updates/updatableAssets query
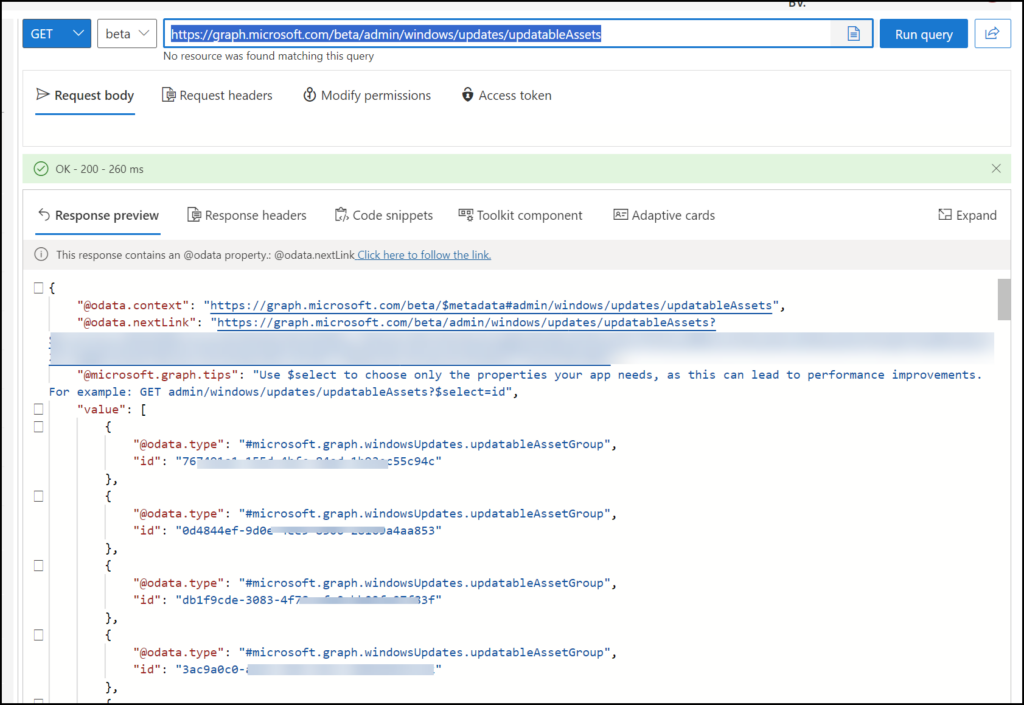
What we can see here is that maybe several devices were not checked into the Windows update service, in this case, every device was correctly in the system. Up to the next step.
Checking if the Telemetry is set
In Intune we can create a policy to send the Telemetry, so we first need to check if the policy is in place and targeted the right way. This telemetry is needed because we as admins will first look at our dashboard where all the data is before going into the device itself. This was the case, and now we need to check if this is also the case on the devices themselves.
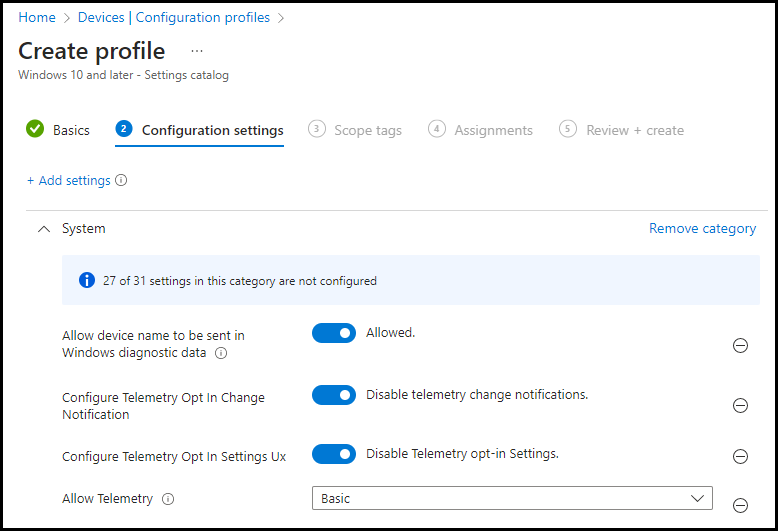
On the device, we went to the registry and checked the following key Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\DataCollection
Check if the Windows Updates CSP is set via Intune
If we go to Intune there we build a Windows update ring to set to our users/devices, all of these settings are being set within the CSP (Configuration Service Provider) in the registry under Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\current\device\Update
So first the Intune settings:
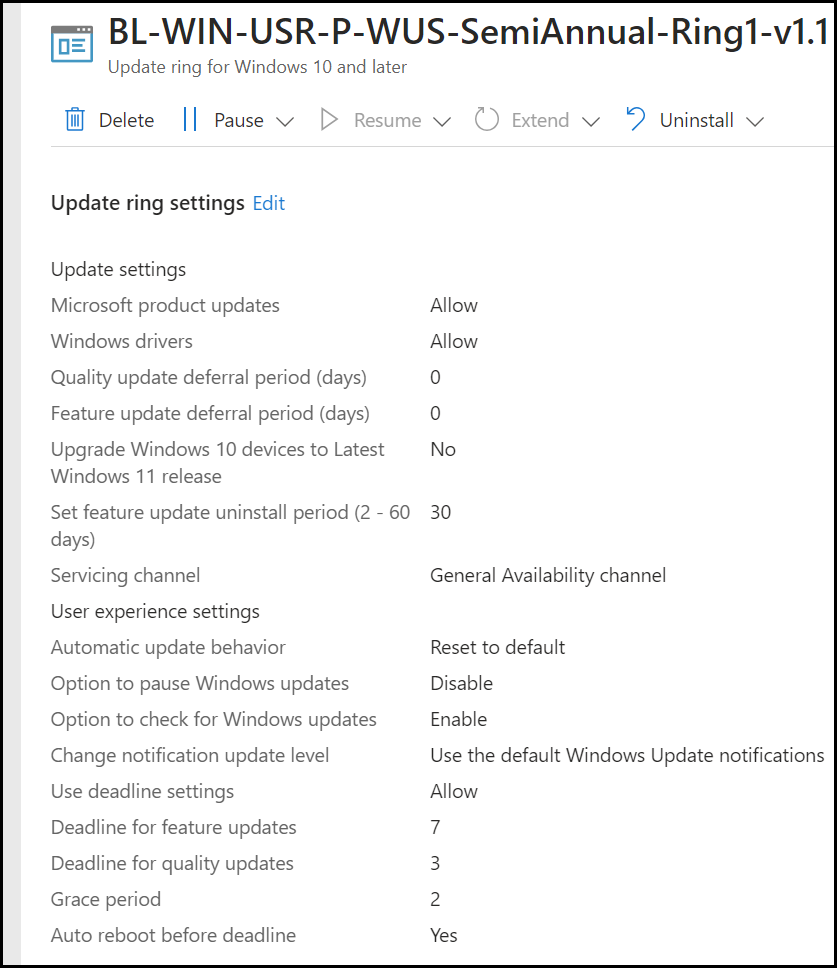
And now the CSP in the registry:
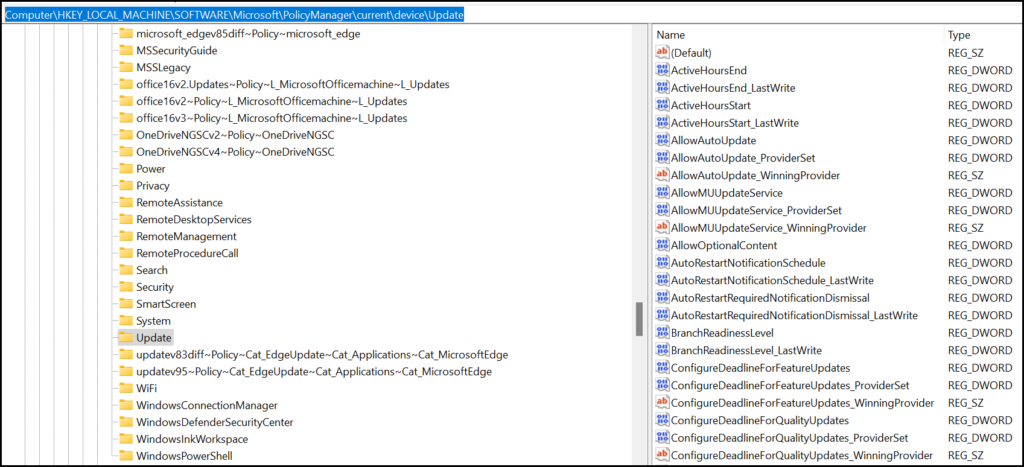
So the conclusion here is that all policies are correctly set and there we didn’t find our issue. Before going it is good the create a bigger warning here.
WARNING: MDM Wins Over GPO does NOT apply to the Windows Update policies.
Check Windows Updates on the device
Because we have checked the basics of the Windows Update service we need to go more into the device. So maybe there lies our problem, we got also devices that came from a third-party supplier with similar issues.
In Windows 11 we can see which policies are running on a device, by going to Start | Settings | Windows Update | Advanced Options | Configurered update policies. Here we will see the setting and what type, in an Intune CSP situation we will see only the type Mobile Device Management and not Group policy.
Now with these devices, this is what we see in the settings.
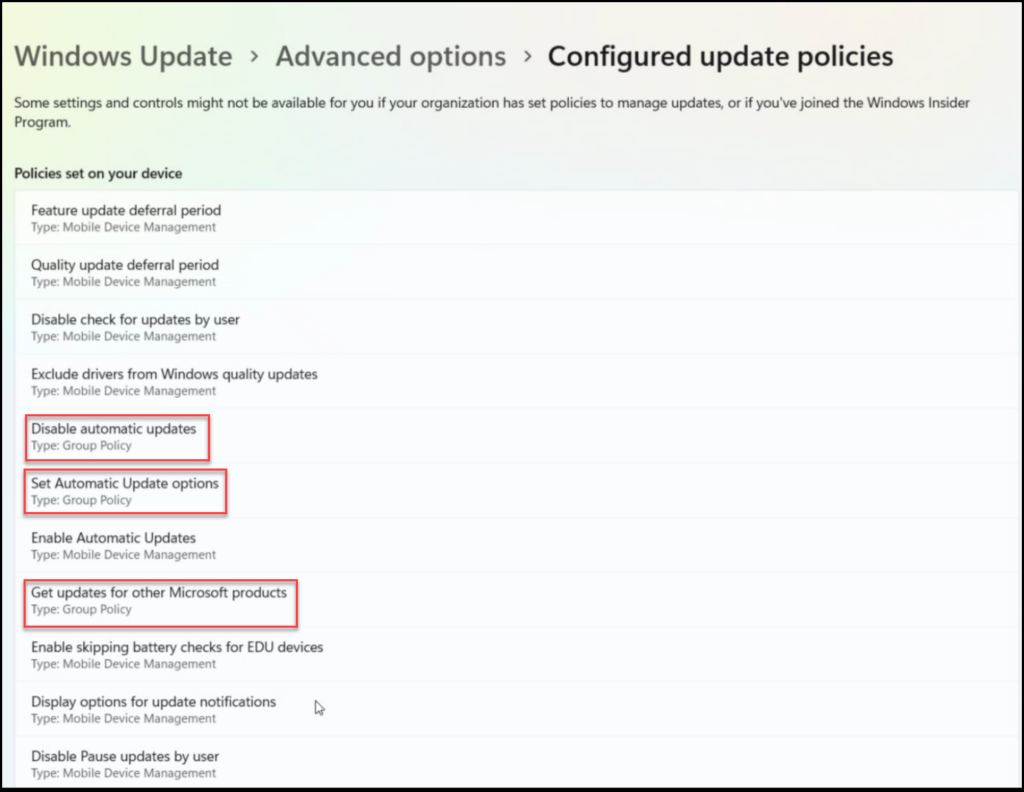
So that is not what we would like to see for an Intune-only managed device. These devices were installed via an external MDT with a WSUS task in it. This might be the issue, but never had any issues before so we need to dig a little further.
Getting into Group Policies Windows Updates
If we go into the place where the Group policy would host it in the registry, in this doc we can find the place https://learn.microsoft.com/en-us/windows/deployment/update/waas-wu-settings#configuring-automatic-updates-by-editing-the-registry
So we will need to have a look into the registry
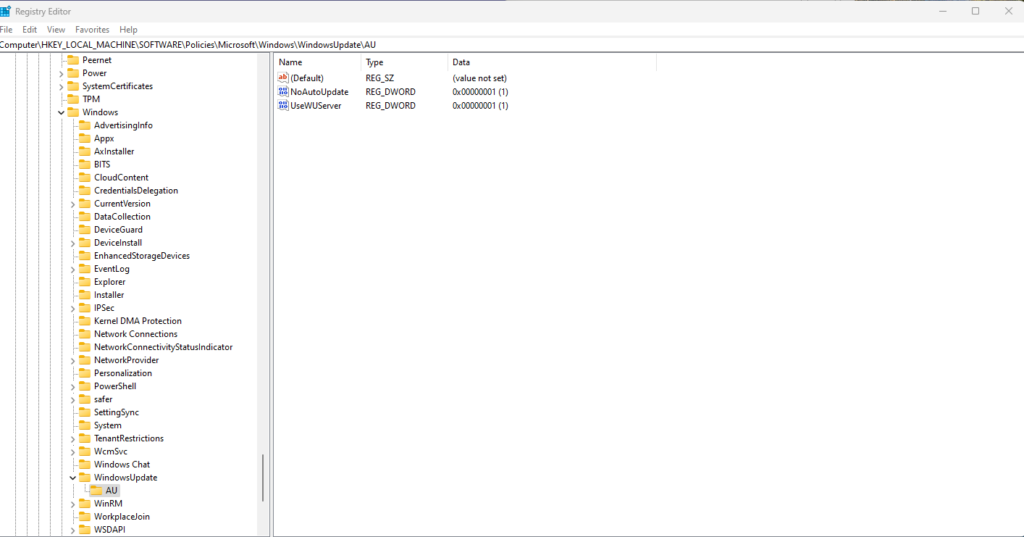
Oke this is not normal, this should be nice and clean to have Intune with the Windows update service do all its tricks.
But how can we solve this, without going to all the devices and fixing the issue?
Remediation
To have a nice clean device without GPO policies, we need to clean the device. In a normal situation, a device comes from a supplier and is in a nice clean condition (oke sometimes those annoying bloatware). In an imaging situation in one of the task sequences the device will be cleaned, often by cleaning the WindowsUpdate registry path
Because the devices are already with users and up and running in a production environment, we can use a remediations script to resolve this, keep in mind we need a minimal Microsoft 365 F3, E3, or E5 license to be able to run it.
Go to Devices | Scripts and remediations click on +Create
Fill in a name and click Next
Now we need to add the scripts to detect and remediate the first step of the detect script.
Copy and paste the script below create the ps1 file and click on Select a file
Detection
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
#============================================================================================================================= # # Script Name: Detect_WIndowsUpdateRegkey.ps1 # Description: Detect HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate AU Key # # Notes: Detect if the key AU is available under HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate if output # is 1 this wil be remediated. #============================================================================================================================= # Define the registry path $registryPath = "HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU" # Check if the registryd key exists if (Test-Path -Path $registryPath) { Write-Output "The 'AU' key exists" exit 1 } else { Write-Output "The 'AU' key does not exist" exit 0 } |
Copy and paste the script below create the ps1 file and click on Select a file
Remediate
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
#============================================================================================================================= # # Script Name: Remediate_WIndowsUpdateRegkey.ps1 # Description: Detect HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdat AU Key # # Notes: AU is available and will be removed #============================================================================================================================= # Define the registry path $registryPath = "HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU" Remove-Item -Path $registryPath -Recurse |
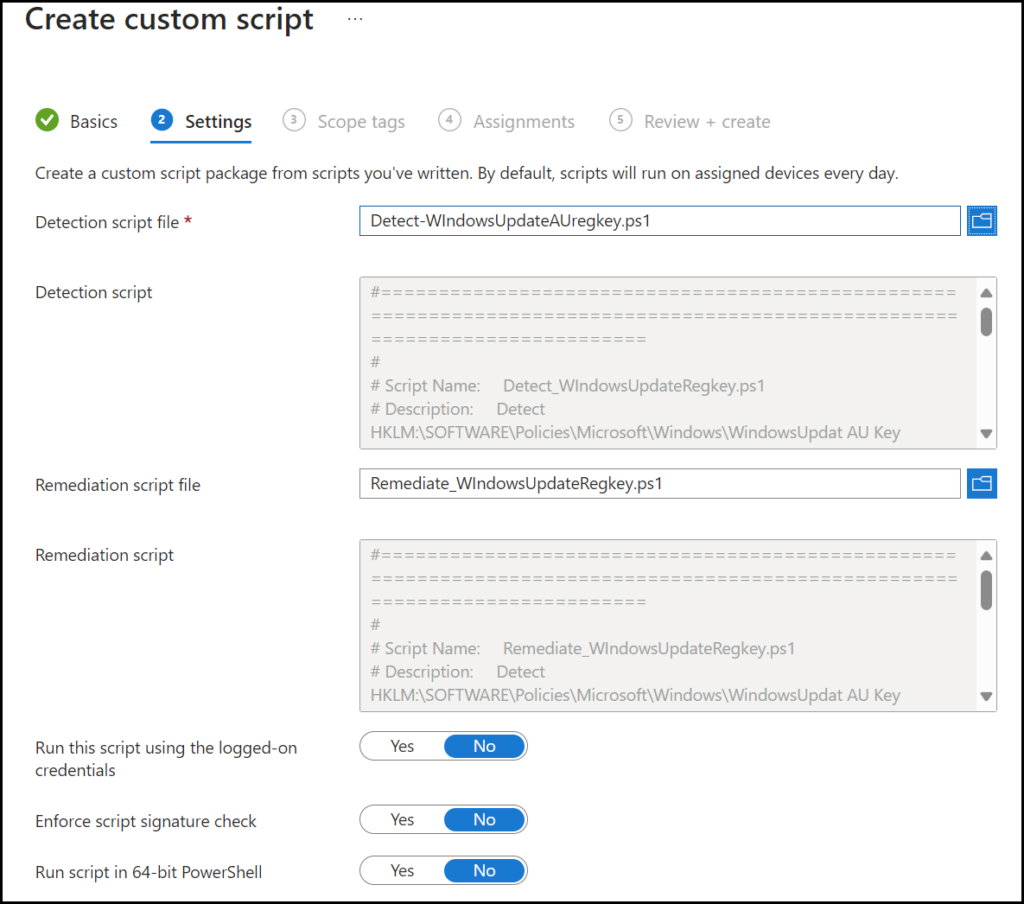
Leave the slider like the picture above, click Next, and add an assignment, in the assignment of the remediation script we can set a schedule of you’re liking. And we are off.
[…] Troubleshooting Windows Updates (WUfB): GPO policy snags […]