Microsoft Intune’s ability to manage and enforce policies on devices relies heavily on the Open Mobile Alliance Device Management (OMA-DM) protocol. This XML-based, lightweight protocol is at the heart of how Intune configures devices, deploys policies, and ensures compliance. Beyond setting policies, Intune employs a robust Get-Set-Get process to verify their application. In this blog, we’ll break down how Intune uses OMA-DM, how it sets policies, and the mechanisms to validate if those policies are properly enforced.
What is OMA-DM?
OMA-DM is a standardized protocol designed for remote device management. Its design makes it widely used in mobile device management (MDM) solutions. Within the Windows ecosystem, OMA-DM operates via Configuration Service Providers (CSPs)—specialized APIs that map Intune’s policies and commands to actionable instructions for the device.
In simpler terms, CSPs act as the bridge between the Intune cloud service and the local device settings. For example:
- Configuring a password policy? Intune communicates with the ./Vendor/MSFT/Policy/Config/DeviceLock CSP.
- Enforcing encryption? Intune interacts with the ./Vendor/MSFT/BitLocker CSP.
How Intune Sets Policies Using OMA-DM
When an Intune administrator creates a policy, the following sequence occurs:
- Policy Creation in Intune
Administrators define configurations or compliance policies within the Intune admin center. - Policy Conversion
Intune converts these policies into OMA-DM XML commands. Each command is directed to the appropriate CSP node on the device. - Policy Deployment
Intune pushes these commands to devices via the OMA-DM client, which is built into Windows. - Policy Application on Device
The OMA-DM client processes the commands and makes the necessary changes to the device. These changes are often reflected in the Windows registry or local policy files.
Example: To enforce a password requirement, Intune writes to the ./Vendor/MSFT/Policy/Config/DeviceLock CSP. This change is applied to the corresponding registry key under HKLM\SOFTWARE\Microsoft\PolicyManager\.
How Intune checks policy application using the “Get-Set-Get” Method
One of the critical mechanisms Intune uses to validate policy application is the Get-Set-Get process. This method ensures that policies deployed via OMA-DM are successfully applied and remain consistent on the device.
Understanding the Get-Set-Get Process
The Get-Set-Get workflow is a three-step interaction between the Intune service and the device. Here’s how it works:
- First “Get” (Initial Query)
Intune queries the device by sending aGETcommand to the relevant CSP node. This step checks the current state or value of a policy before applying any changes.- Purpose: To ensure the device’s baseline configuration is understood and identify if the policy is already applied.
- Set (Policy Deployment)
If the initial query reveals that the policy is not yet applied, Intune sends aSETcommand to the CSP node. This command updates the configuration on the device. - Second “Get” (Validation Query)
After applying theSETcommand, Intune performs a follow-upGETto the same CSP node to verify that the policy change was successfully applied.- Purpose: To confirm that the desired value is now reflected on the device, ensuring policy enforcement.
Example: Get-Set-Get in Practice
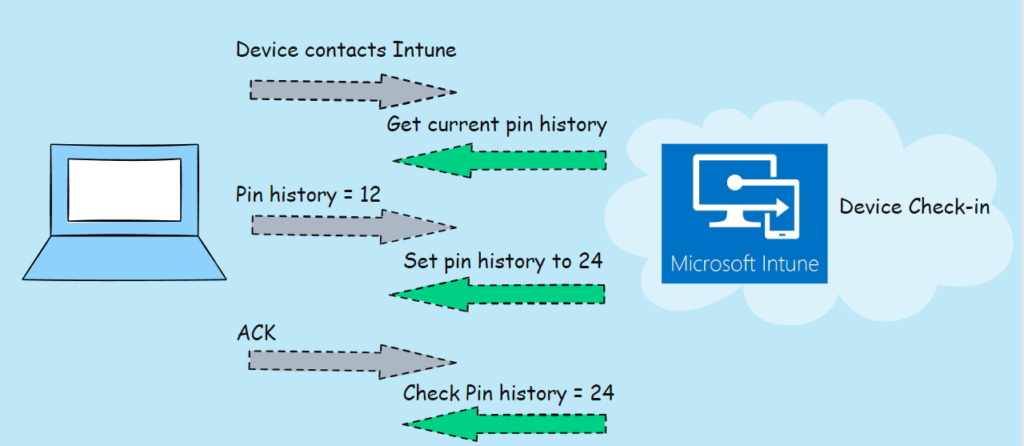
Let’s walk through an example of enforcing a device password using the Get-Set-Get method, with this example we setting an policy where we set the Device Lock with a device password history of 24.
First Get:
Intune queries the ./Vendor/MSFT/Policy/Config/DeviceLock/DevicePasswordHistory CSP. The device reports back false (pin history not set (correct) ).
Set:
Intune sends a SET command to enable DevicePasswordHistory
now with the SyncMLViewer tool from Oliver Kieselbach we can see the command coming down to the device
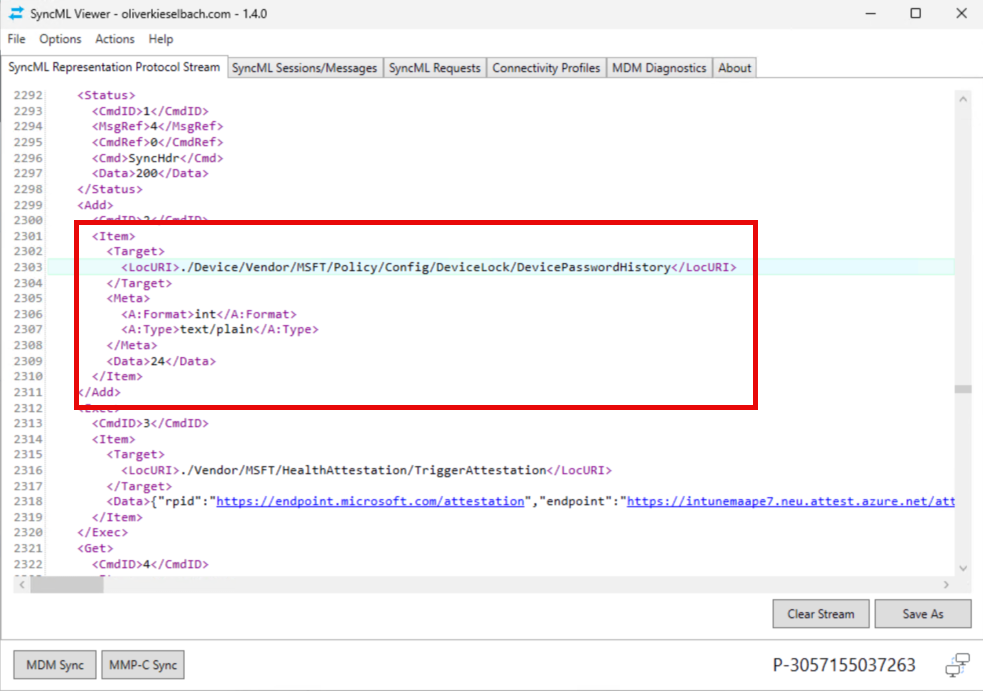
Second Get:
Intune performs a follow-up GET to confirm that DevicePasswordHistorytrue. If not, the device is flagged for remediation.
how will this look in a flow
Conclusion
OMA-DM provides the backbone for Intune’s current policy management, while the Get-Set-Get method ensures policies are not only applied but also validated. Understanding these processes is key to maintaining compliance and security in modern device management. How OMA-DM deliver is a first step because Microsoft is going to use MMP-C to deliver policies to our devices, we will explain this in an following blogpost.

[…] OMA-DM policies rely on SyncML, an XML-based format for defining configurations. While SyncML is […]