The last couple of days a vulnerability came along called “Follina”, which uses Word’s external link to load the HTML and then uses the “ms-msdt” scheme to execute PowerShell code. Microsoft just released a CVE for it an can be found here
it’s states it can be solved by creating a ASR rule from endpoint manager
Table of Contents
Create a ASR Rule
Go to Endpoint Manager and click on Endpoint Security (Step 1)
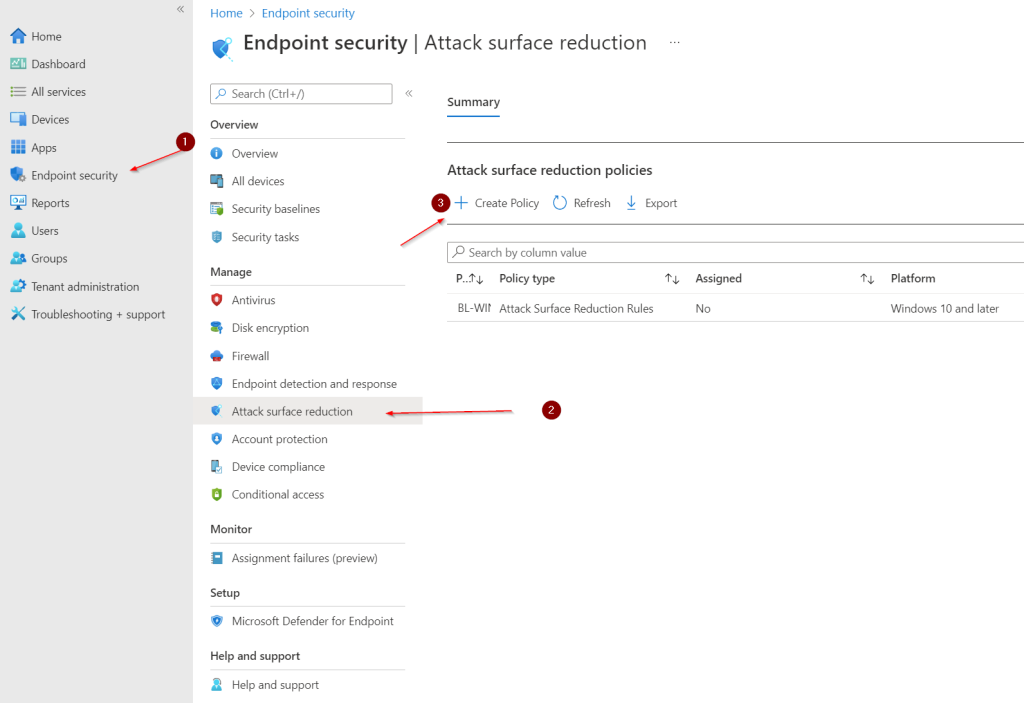
Click on Attack surface reduction (step 2)
Click on Create Policy
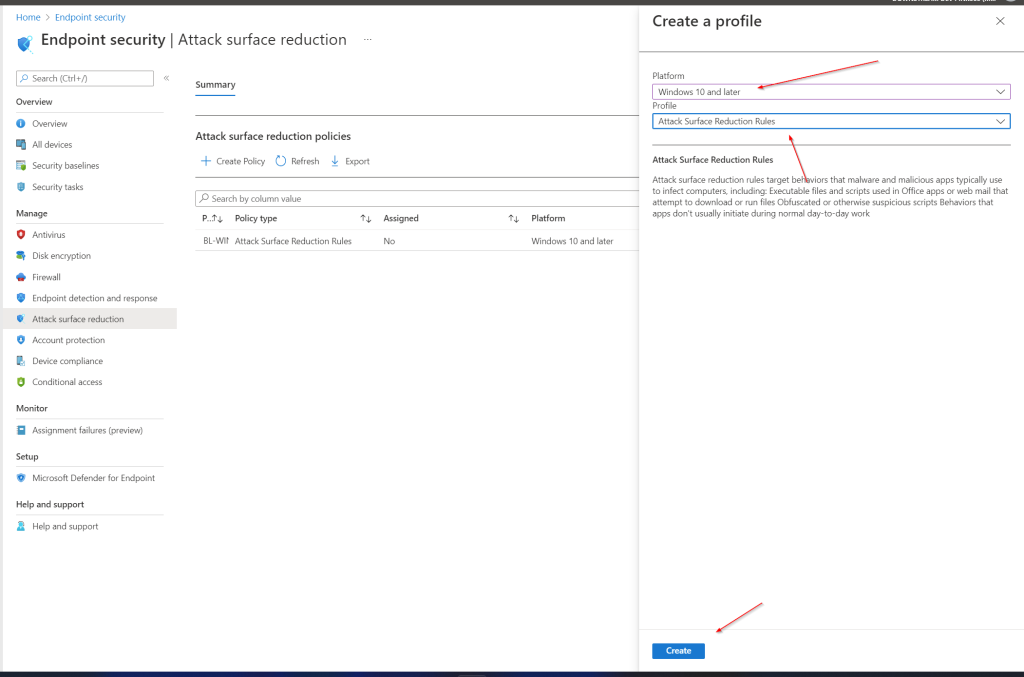
Policy
Fill in Platform Windows 10 and later
Profile Attack Surface Reduction Rules an click Create
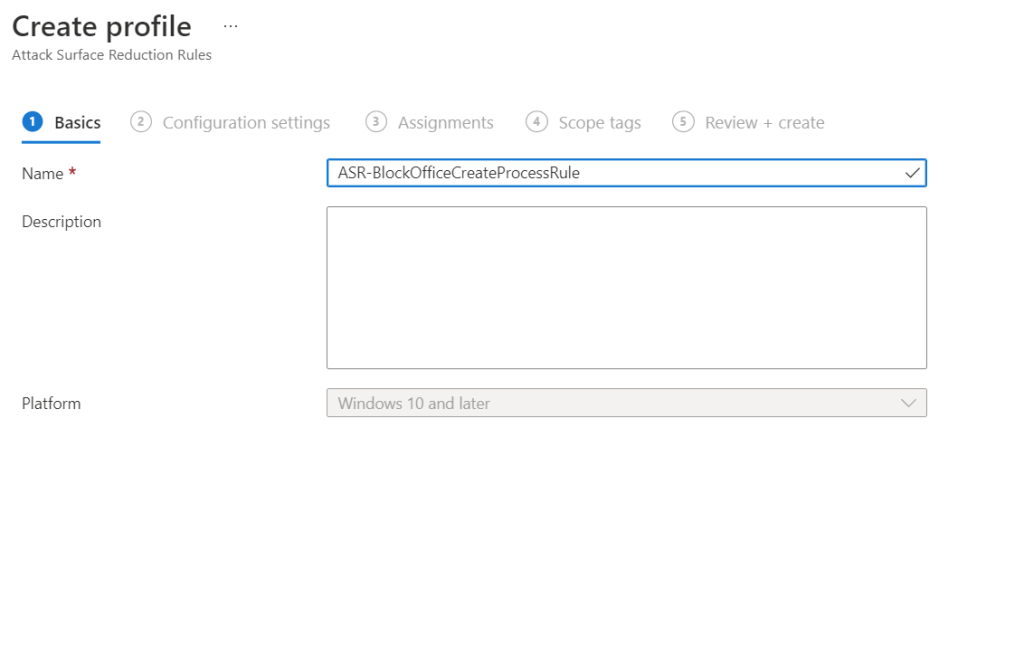
Fill a policy name and click Next
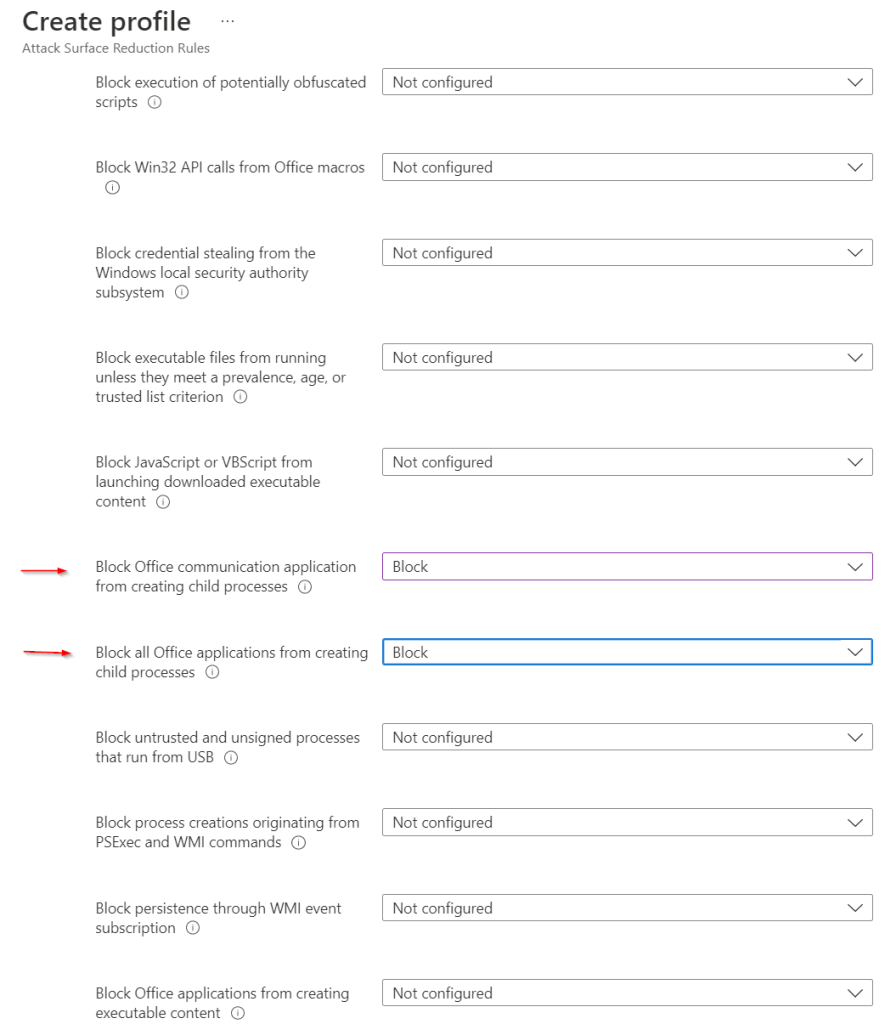
Set the following rules to Block:
- Block Office communication application from creating child processes
- Block all Office applications from creating child processes
Click next and assign to the appropriate group in you’re environment.
