Managing user privileges effectively is crucial in today’s security landscape. Microsoft Intune’s Endpoint Privilege Management (EPM) is designed to handle this by allowing users to request elevated privileges without needing full admin rights. However, the current process has some limitations—particularly when it comes to the speed and communication involved in approving these requests. It might be helpful to get an elevation request notification.
Elevation Request Handling in Microsoft Intune
As organizations increasingly adopt Microsoft Intune for managing endpoints, one of the challenges that often arises is handling administrative privilege elevation requests. With the introduction of Endpoint Privilege Management (EPM) in Intune, admins can set policies that allow users to request elevated privileges for specific applications or tasks. Managing user privileges effectively is crucial in today’s security landscape. Microsoft Intune’s Endpoint Privilege Management (EPM) is designed to handle this by allowing users to request elevated privileges without needing full admin rights.
The Challenges of Support-Approved File Elevations
Support-approved file elevations in EPM allow users to request the permissions they need to complete specific tasks. An IT administrator then reviews these requests through the Intune portal. While this ensures security, the process can be slow and cumbersome. Requests might sit unnoticed in the portal, leading to delays, and users are left in the dark about their requests’ status.
We can leverage Azure Logic Apps to automate the process, ensuring administrators are promptly notified of pending elevation requests and can respond on time. In this post, I’ll walk you through the steps to set up an automated workflow using Logic Apps that retrieves pending elevation requests, sends notifications via Microsoft Teams, and allows quick approvals or denials.
Why Automate EPM elevation request notifications?
Without automation, handling elevation requests can be a manual, time-consuming process:
- Admins must regularly check the Intune portal to identify pending requests.
- Delays in responding to requests can impact user productivity, especially when admin privileges are needed for urgent tasks.
- Overlooked requests can lead to security and compliance issues if users are granted more privileges than necessary.
By automating the notification and approval process, we can significantly reduce the time it takes to respond to these requests, improving both security and operational efficiency.(After some talks with Peter Klapwijk, I decided to full swing for the first time into logic app)
Prerequisites for creating an elevation request notification:
Before we dive into the implementation, there are a few prerequisites you’ll need:
- Access to Microsoft Azure Portal – Ensure you have the necessary permissions to create and manage Logic Apps and a subscription
- Microsoft Graph API Permissions—We are going to create a managed identity with the correct permissions. We can also use a key vault, but a managed identity is generally considered more secure and easier to manage.
- Permissions
- DeviceManagementConfiguration.Read.All
- DeviceManagementConfiguration.ReadWrite.All
- Permissions
- Microsoft Teams Setup – Admins should have access to Microsoft Teams, where notifications will be sent.
Step-by-step implementation
Step 1
Let’s walk through the steps to create an Azure Logic App that will automate handling elevation request notifications.
Create a managed identity.
We can use Getting started with Logic Apps: Part 4—Secure MS Graph queries with a system-assigned managed identity | Syst & Deploy (systanddeploy.com) to create the right permissions for the Logic App’s managed identity.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
# Your tenant id (in Azure Portal, under Azure Active Directory -> Overview ) $TenantID="Your tenant id" # Name of the manage identity or enterprise application $DisplayNameOfMSI="EPM_Elevation_requests in our case" # Check the Microsoft Graph documentation for the permission you need for the operation $PermissionName = "DeviceManagementManagedDevices.ReadWrite.All" # Permission to set to the managed identity $Permissions = @( 'DeviceManagementConfiguration.Read.All', 'DeviceManagementConfiguration.ReadWrite.All' ) # Check if module is installed and if not install it If(!(Get-Installedmodule Microsoft.Graph.Applications)){Install-Module Microsoft.Graph.Applications}Else{Import-Module Microsoft.Graph.Applications} # Authenticate Connect-MgGraph -Scopes Application.Read.All, AppRoleAssignment.ReadWrite.All, RoleManagement.ReadWrite.Directory -TenantId $TenantID # Get info about the managed identity $MSI = Get-MgServicePrincipal -Filter "displayName eq '$DisplayNameOfMSI'" $API = Get-MgServicePrincipal -Filter "displayName eq 'Microsoft Graph'" # Check permissions to add $AppRoles = $API.AppRoles | Where-Object {($_.Value -in $Permissions) -and ($_.AllowedMemberTypes -contains "Application")} # Set permissions ForEach($Role in $AppRoles){ New-MgServicePrincipalAppRoleAssignment -ServicePrincipalId $MSI.Id -PrincipalId $MSI.Id -AppRoleId $Role.Id -ResourceId $API.Id } |
Create an Azure Logic App
- Navigate to the Azure Portal:
- Go to Azure Portal.
- Select Create a Resource and choose Logic App from the available services.
- Configure the Logic App:
- Provide a name for your Logic App. In our case, we are going to use EPM_Elevation_requests.
- Please select the desired subscription, resource group, and location; in this case, we use consumption.
- Click Review + Create and then Create to set up the Logic App.
Define the Workflow Trigger
We want our Logic App to check for pending elevation request notification very 15 minutes. To achieve this, we set up a Recurrence trigger.
Add a New Trigger recurrence:
- In the Logic App Designer, select Recurrence as the trigger.
- Set the frequency to Minutes and the interval to 15.
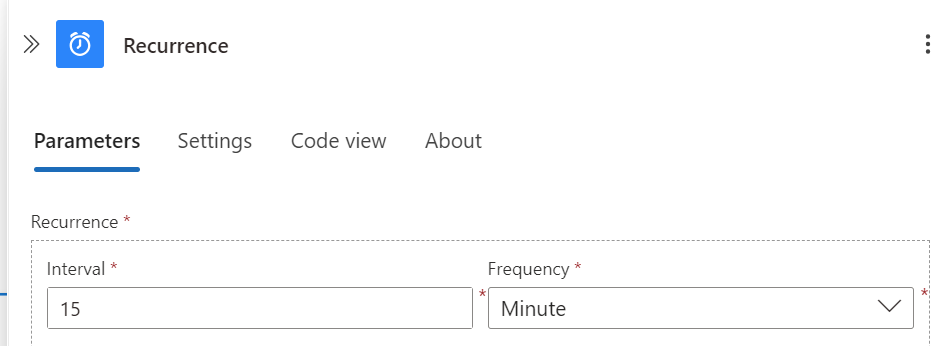
This trigger will ensure the workflow runs every 15 minutes to check for new elevation request notification.
Query Pending Elevation Requests
Next, we must query the Microsoft Graph API to retrieve all pending elevation requests. Because we wanted only the information about 15 minutes ago, we are adding an extra function.
Add an HTTP Action:
Choose HTTP as the next step.
- Configure the authentication type to Managed Identity and Audience (https://graph.microsoft.com).
- Set the Method to GET.
- Use the following URI to query pending requests
https://graph.microsoft.com/beta/deviceManagement/elevationRequests?$filter=(Status%20eq%20'pending')with the added function formatDateTime(addMinutes(utcNow(),-15),’yyyy-MM-ddTHH:mm:ssZ’)
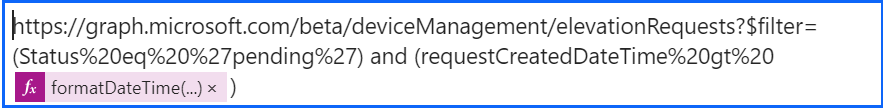
- Configure the Authentication type as Managed identity and audience (https://graph.microsoft.com).
This step will fetch all pending elevation request notifications from Intune.
Parse the JSON Response
After retrieving the pending requests, we need to parse the response to extract relevant information:
Add a Parse JSON Action:
Set the Content to the body of the HTTP response.
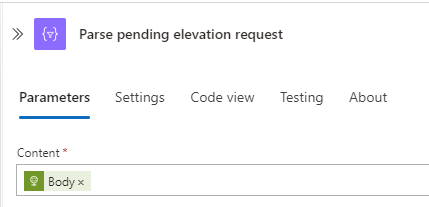
Define the schema to match the structure of the elevation request notification copy and paste it from below.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 |
{ "properties": { "@@microsoft.graph.tips": { "type": "string" }, "@@odata.context": { "type": "string" }, "value": { "items": { "properties": { "applicationDetail": { "properties": { "fileDescription": { "type": "string" }, "fileHash": { "type": "string" }, "fileName": { "type": "string" }, "filePath": { "type": "string" }, "productInternalName": { "type": "string" }, "productName": { "type": "string" }, "productVersion": { "type": "string" }, "publisherCert": { "type": "string" }, "publisherName": { "type": "string" } }, "type": "object" }, "deviceName": {}, "id": { "type": "string" }, "requestCreatedDateTime": { "type": "string" }, "requestExpiryDateTime": { "type": "string" }, "requestJustification": { "type": "string" }, "requestLastModifiedDateTime": { "type": "string" }, "requestedByUserId": { "type": "string" }, "requestedByUserPrincipalName": { "type": "string" }, "requestedOnDeviceId": { "type": "string" }, "reviewCompletedByUserId": { "type": "string" }, "reviewCompletedByUserPrincipalName": {}, "reviewCompletedDateTime": {}, "reviewerJustification": {}, "status": { "type": "string" } }, "required": [ "id", "requestedByUserId", "requestedOnDeviceId", "requestedByUserPrincipalName", "deviceName", "requestCreatedDateTime", "requestLastModifiedDateTime", "requestJustification", "status", "reviewCompletedByUserId", "reviewCompletedByUserPrincipalName", "reviewCompletedDateTime", "requestExpiryDateTime", "reviewerJustification", "applicationDetail" ], "type": "object" }, "type": "array" } }, "type": "object" } |
This action will parse the JSON response and make working with individual elevation request notification details easier.
Summary Step 1
We have now completed the first part of the Logic App
- Recurrence every 15 min
- Get HTTP, here we get the elevation request notification from the Graph and using only data from the last 15 min
- Parsing this information so we can handle the data
It will look like this:
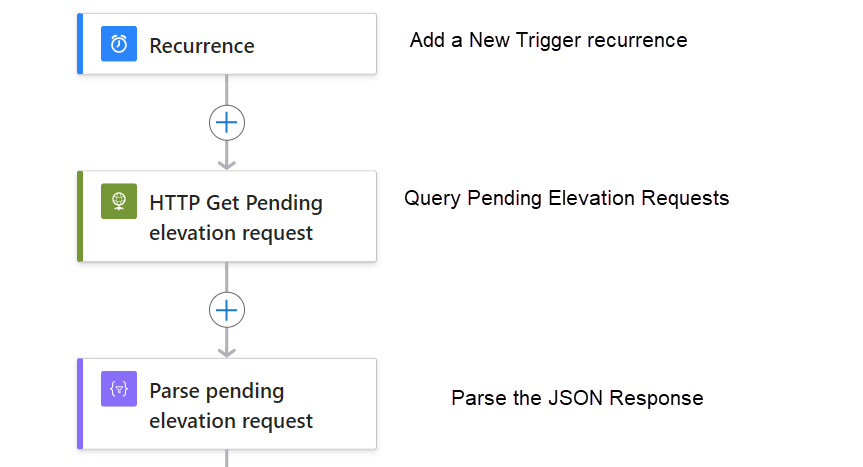
Step 2
Loop Through Each Elevation Request notification
To handle each request individually, we use a For each
- Add a Foreach Loop:
- Select For each as the next step.
- Set the output to the parsed JSON
bodyvalue.
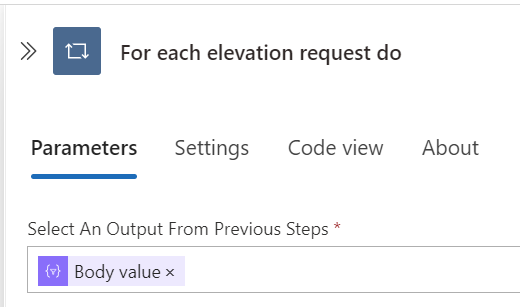
This loop will iterate over each elevation request notification returned from the Microsoft Graph API.
Send Notification via Microsoft Teams
We can create an adaptive card via adaptivecards.io. To do so, we need to choose the host app Teams and click on New card. Starting fresh we can create a personal one or use mine instead
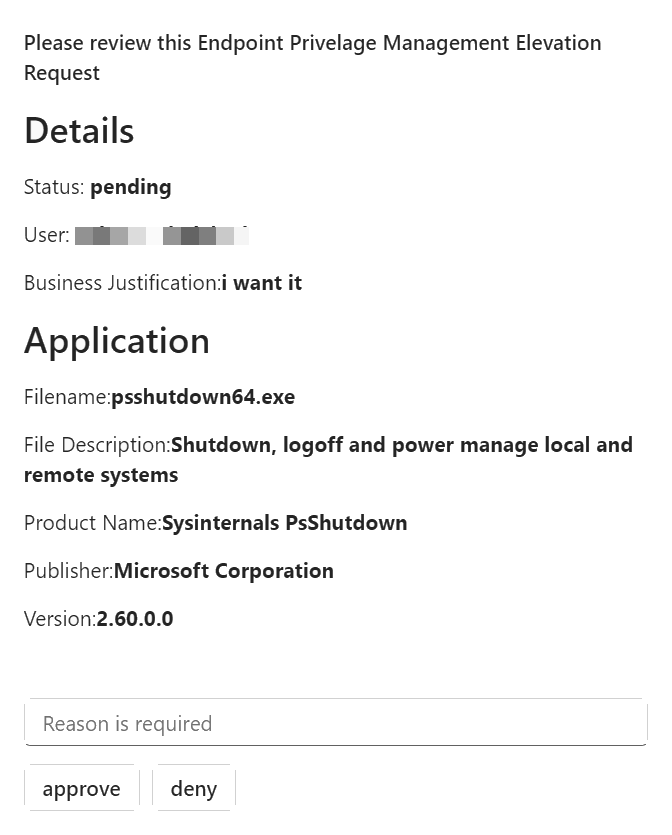
Within the loop, we send an Adaptive Card to a Microsoft Teams channel or individual user to notify the admin of a pending elevation request notification:
- Add an Action Post adaptive card and wait for a response:
- Choose Post an adaptive card and wait for a response (Teams).
- Set up the connection to Microsoft Teams. (fill in the admin credentials for the Teams connection)
In the Post adaptive card and wait for a response we need to fill in the following items Post As Flow Bot (This can also be a channel but will give the admin a better push notification)

Choose a recipient (admin who receives the push notification)
Now comes the part were are adding the adaptive card this needs to be done in the message field
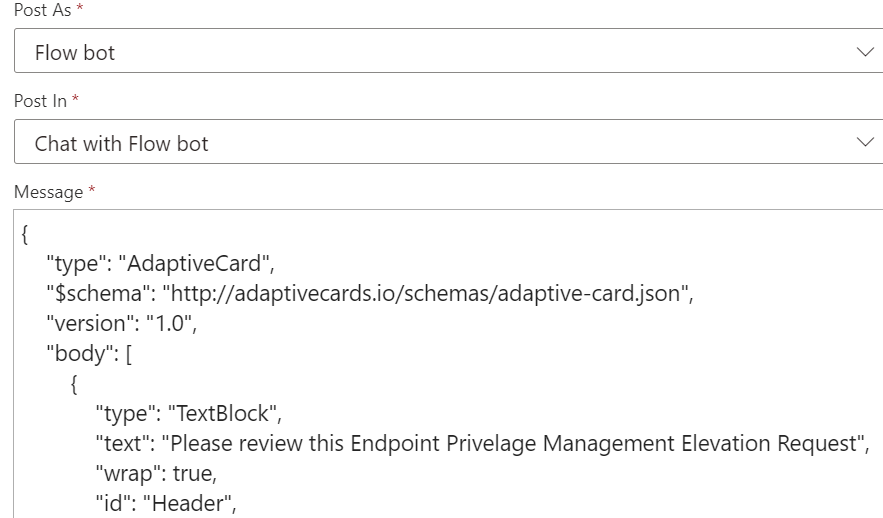
Copy and paste the following
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 |
{ "type": "AdaptiveCard", "$schema": "http://adaptivecards.io/schemas/adaptive-card.json", "version": "1.0", "body": [ { "type": "TextBlock", "text": "Please review this Endpoint Privelage Management Elevation Request", "wrap": true, "id": "Header", "size": "Medium", "weight": "Bolder", "color": "Dark" }, { "type": "TextBlock", "text": "Details", "wrap": true, "size": "ExtraLarge", "color": "Dark", "weight": "Bolder", "isSubtle": false, "id": "Details" }, { "type": "TextBlock", "text": "Status: **@{items('For_each_elevation_request_do')?['status']}**", "wrap": true }, { "type": "TextBlock", "text": "User: **@{items('For_each_elevation_request_do')?['requestedByUserPrincipalName']}**", "wrap": true }, { "type": "TextBlock", "text": "Business Justification:**@{item()?['requestJustification']}**", "wrap": true }, { "type": "TextBlock", "text": "Application", "wrap": true, "size": "ExtraLarge", "weight": "Bolder", "color": "Dark", "id": "application" }, { "type": "TextBlock", "text": "Filename:**@{item()?['applicationDetail']?['fileName']}**", "wrap": true }, { "type": "TextBlock", "text": "File Description:**@{item()?['applicationDetail']?['fileDescription']}**", "wrap": true }, { "type": "TextBlock", "text": "Product Name:**@{items('For_each_elevation_request_do')?['applicationDetail']?['productName']}**", "wrap": true }, { "type": "TextBlock", "text": "Publisher:**@{items('For_each_elevation_request_do')?['applicationDetail']?['publisherName']}**", "wrap": true }, { "type": "TextBlock", "text": "Version:**@{items('For_each_elevation_request_do')?['applicationDetail']?['productVersion']}**", "wrap": true }, { "type": "TextBlock", "text": "Path:", "wrap": true }, { "type": "Input.Text", "placeholder": "Reason is required", "isRequired": true, "id": "reasonid" } ], "actions": [ { "type": "Action.Submit", "title": "approve", "id": "approve" }, { "type": "Action.Submit", "title": "deny", "id": "deny" } ] } |
It will look like this:
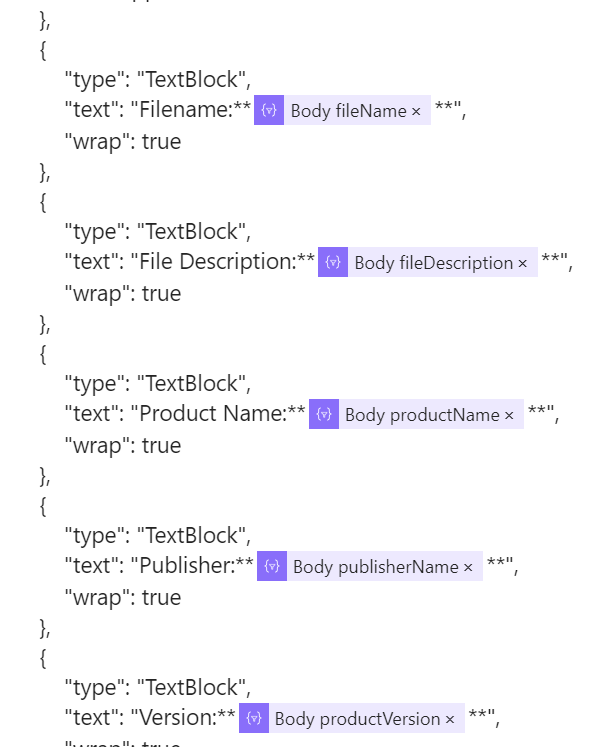
Where the **are used getting the outcome get as bold text, and if we want to change things click on the lightning, now we have the possibility to choose from different data fields gotten from the parsing JSON part.


Summary Part 2
We have now completed the second part of the Logic App
- Created a for each elevation loop (if there are more elevation request notifications, we will send for every request a responsive card
- Created a responsive card waiting for a response to Teams
It will look like this:
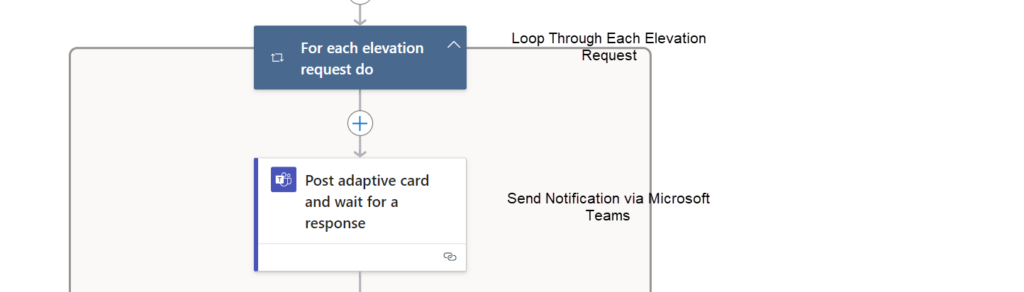
The Admin will see the following if there is an elevation request notification waiting
Step 3
Handle Admin Response
Once the admin responds, we need to handle the response
Add a Parse JSON Action
- Add another Parse JSON action to parse the response from the Adaptive Card.
- Set the content to the response from the Teams action Body.
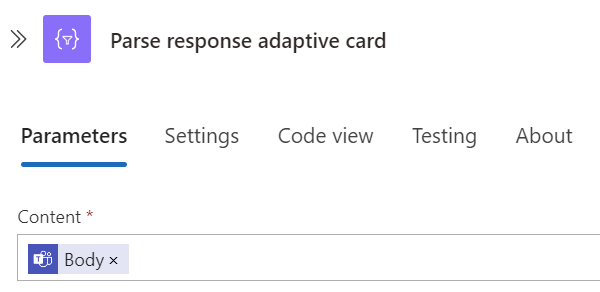
Add the Schema
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 |
{ "properties": { "data": { "properties": { "reasonid": { "type": "string" } }, "type": "object" }, "messageId": { "type": "string" }, "messageLink": { "type": "string" }, "responder": { "properties": { "displayName": { "type": "string" }, "email": { "type": "string" }, "objectId": { "type": "string" }, "tenantId": { "type": "string" }, "userPrincipalName": { "type": "string" } }, "type": "object" }, "responseTime": { "type": "string" }, "submitActionId": { "type": "string" } }, "type": "object" } |
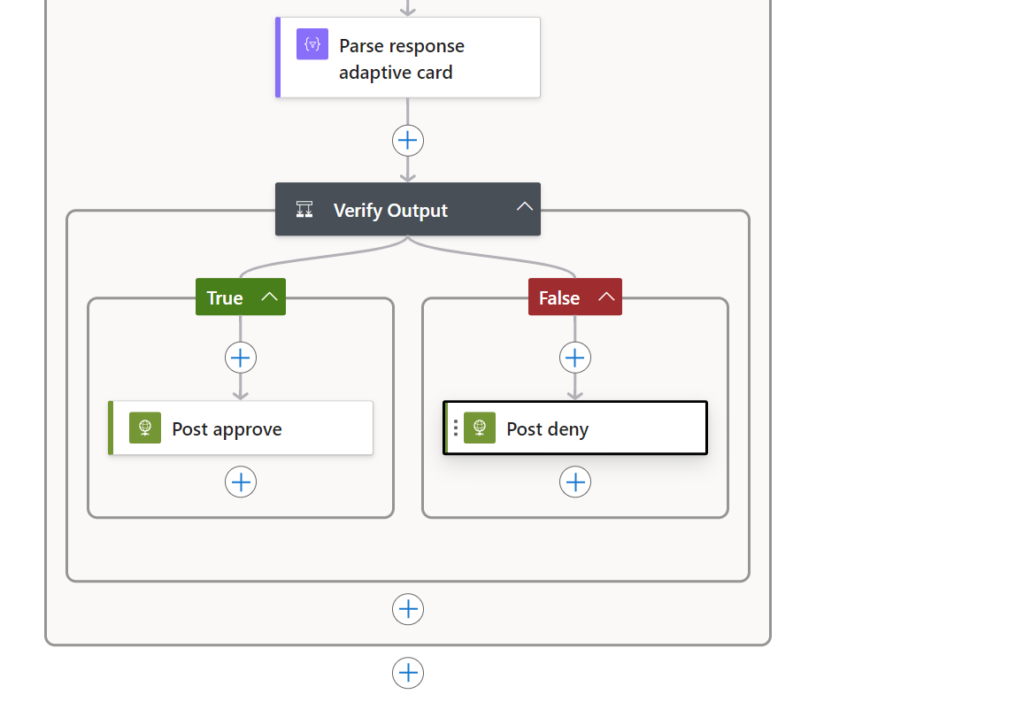
Add a Verify Output to Check Response
Use an and condition to check if the response was Approve or Deny by clicking the lighting again and choose Body submitactionid and set it to is equal to approve
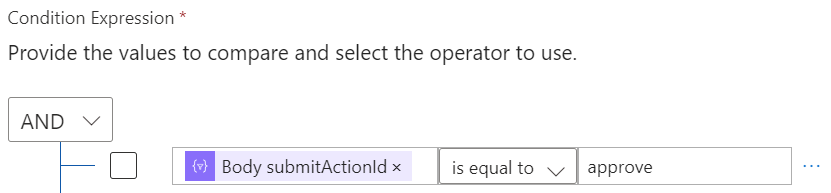
Based on the response, send an HTTP POST request to the Microsoft Graph API to either approve or deny the request.
Approve or Deny the Request via Microsoft Graph API
Add HTTP Actions to Approve/Deny:
If approved, send a POST request to: https://graph.microsoft.com/beta/deviceManagement/elevationRequests('{id}')/approve
This has to be done when receiving a deny on the elevation request notification
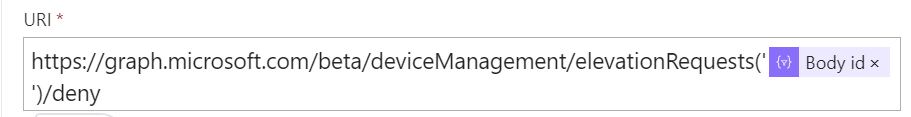
If denied, send a POST request to: https://graph.microsoft.com/beta/deviceManagement/elevationRequests('{id}')/deny
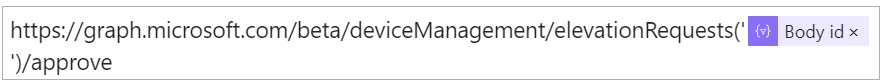
This has to be done when receiving a approve on the elevation request notification
And add in the body the reason like this:
|
1 2 3 |
{ "reviewerJustification": "@{body('Parse_response_adaptive_card')?['data']?['reasonid']}", } |
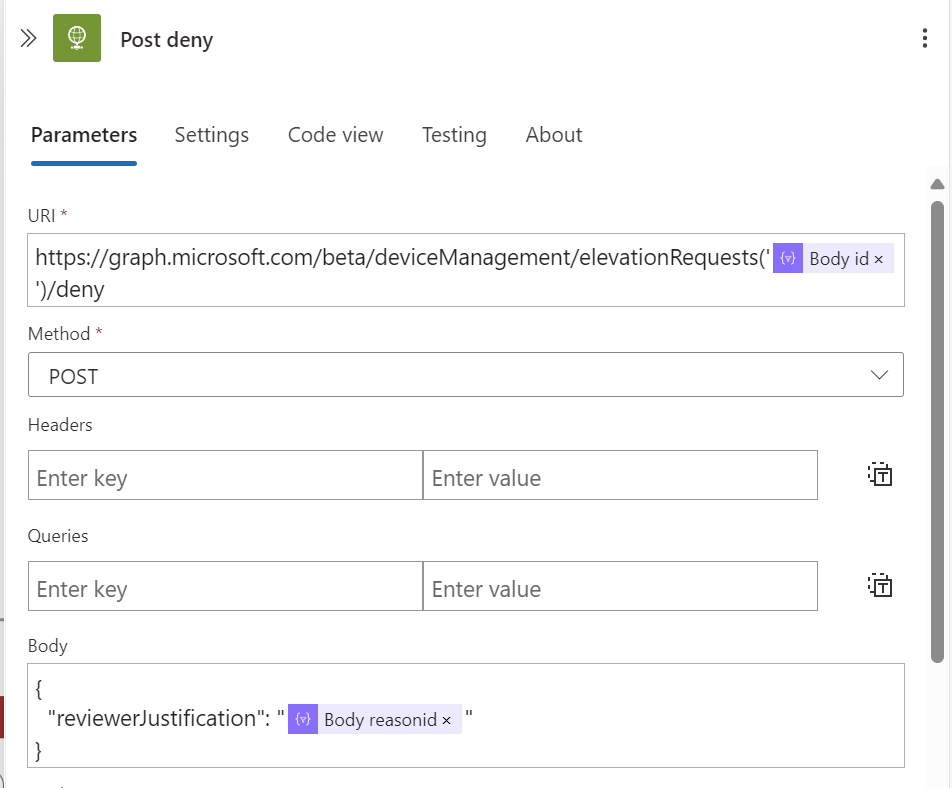
For the authentication use the managed identity again.
Summary Part 3
We have now completed the third part of the Logic App
- Added a Parse JSON Action to handle the response from the admin when pushing the button in the adaptive card
- a verify check which will create a Yes/No action. a Yes will go to the approve flow and the No will go to the deny flow
- Created the HTTP Post action to the graph to approve or deny the elevation request notification
It will look like this:
Experience
We will go through the experience of a user and a admin in 1 go
When going to the Admin portal we will see the elevation request
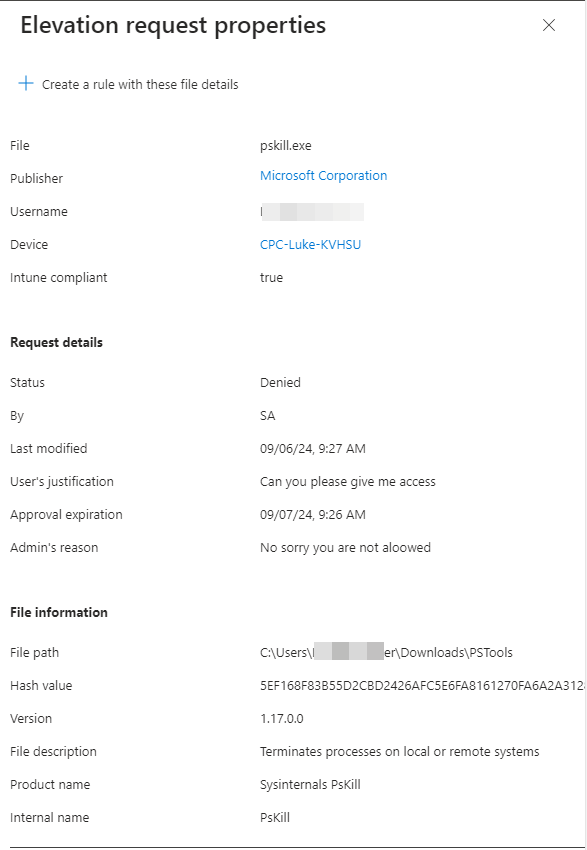
Auditing
Because Endpoint Privilege Management auditing is a vital practice for any organization aiming to enhance its cybersecurity posture. We also needed to check how auditing would workout with the Logic App, when checking te auditing logs we will see the application made the activity
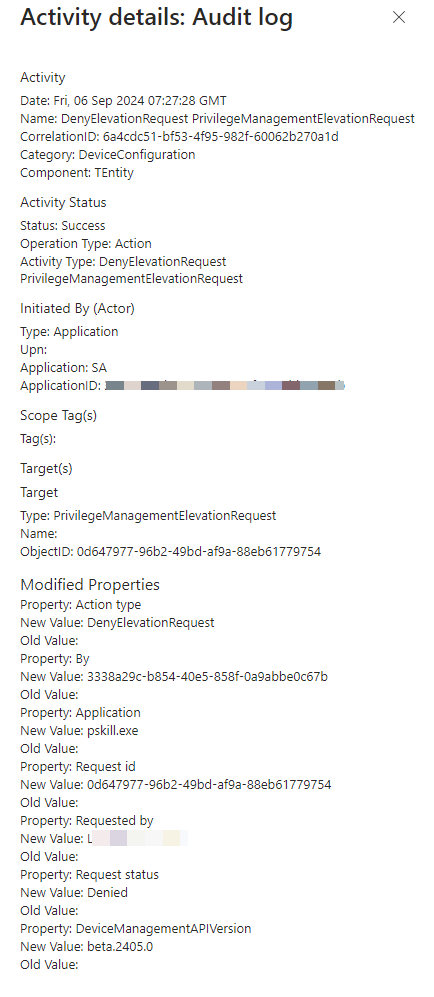
Conclusion
By implementing this Azure Logic App, you automate the entire workflow of handling elevation requests notifications in Microsoft Intune. This automation ensures that admins are promptly notified of any pending requests, allowing them to make timely decisions and maintain security compliance while minimizing disruptions to user productivity.
By combining the power of Microsoft Graph API, Azure Logic Apps, and Microsoft Teams, you can create a streamlined, efficient, and secure process for managing administrative privilege elevation request notifications in your organization.

[…] Get an EPM elevation request notification! – Just about the Modern Workplace (joostgelijsteen.… […]