This blog post will provide a detailed guide for Intune engineers on performing basic MDM hardening and strategies for taking it to the next level. We’ll also explore the key steps in securing your Windows devices, such as configuring enrollment policies, setting up enrollment restrictions, and enforcing conditional access policies. This is going to be a small blog series.
Why MDM Hardening
MDM (Mobile Device Management) hardening is necessary to protect your organization’s devices and data from security threats. Windows MDM hardening, in particular, can be an excellent solution for tightening security measures. Using Windows attestation, you can take basic MDM hardening to the next level. Windows attestation is a security feature that ensures your device meets the necessary security requirements before it accesses sensitive resources. This can help protect your organization’s data from unauthorized access or breaches. With Windows MDM hardening, you can ensure your devices and data are more secure and better protected against security threats.
Device Enrollment

Device Enrollment Process
Device enrollment is the mechanism that enables device management for a given device. During enrollment, Intune installs an MDM certificate on the enrolling device.
This MDM certificate establishes communication with the Intune service, allowing Intune to enforce your organization’s policies.
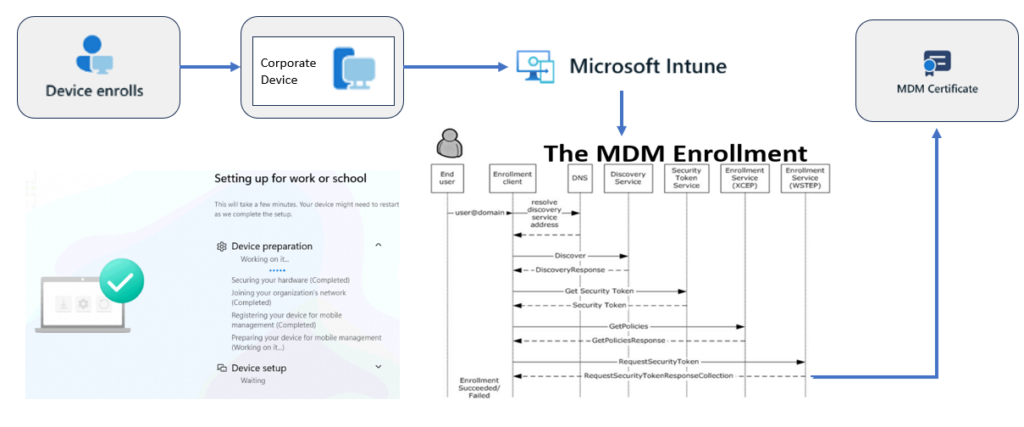
The MDM certificate is stored in the personal computer certificate vault, which will be renewed annually.

It will be renewed by a scheduled task.

If we want to see how this will work in the background, go to the blog post-Rudy created, Preparing your device for mobile device management | Intune (call4cloud.nl)
What we can do in MDM Hardening
In the next steps, we will explore the possibilities for Intune Engineers to set an MDM hardening situation in Intune and the onboarding of a device, whether personal or corporate.
Automatic MDM Enrollment
Intune allows us to enroll our Windows devices automatically when they join or register with your Microsoft Entra ID. You can apply policies, configurations, and apps to your devices without user interaction.
Intune automatic MDM enrollment can be used for both personal and corporate-owned devices, and it supports various scenarios such as bring-your-own-device (BYOD)
By default, these settings are an MDM user scope of All.

MDM user scope is a setting that determines which users can enroll their Windows devices into Intune, a service that allows you to manage and secure your devices. MDM user scope can be set to None, Some, or All. If you set it to None, no users can enroll their devices. If you set it to Some, you can specify which groups of users can enroll their devices. If you set it to All, all users can enroll their devices.
This would be the first step of MDM Hardening. We want to set it to a specific user security group. This will only allow the group of users you are aware of to enroll devices in our tenant.
So we need to go to Devices | Enrollment | Automatic Enrollment and click on Some, Search for the group of users we would like to add to allow MDM enrollment, and click Save (We also like to use the same group for WIP)

Device Platform Restrictions
Device platform restrictions can help Intune MDM Hardening by limiting device enrollment to specific device platforms. This can be useful if, for example, your organization only supports certain types of devices or if you want to restrict access to sensitive resources for specific device platforms. By setting device platform restrictions, you can ensure that only approved and secure devices are enrolled in your organization’s MDM solution. In these policies, we can block personal devices and allow corporate devices. This can help to reduce the risk of security breaches and data loss.
Creating specific platform restriction
To set this setting, we need to go to Devices | Enrollment | Device Platform Restrictions and click on + Create restriction; give it a name and a description of what you like.

Click on Next. Now comes the policy, where we can block or allow specific device ownership and builds. What we would like to achieve is blocking personal devices from being onboarded to Intune to keep the data on our devices safe; therefore, we are only allowing corporate devices from a Windows N-1 build.
- Windows 10 21h2= 10.0.1944
- Windows 11 22h2 = 10.0.22621
Now, how will this look
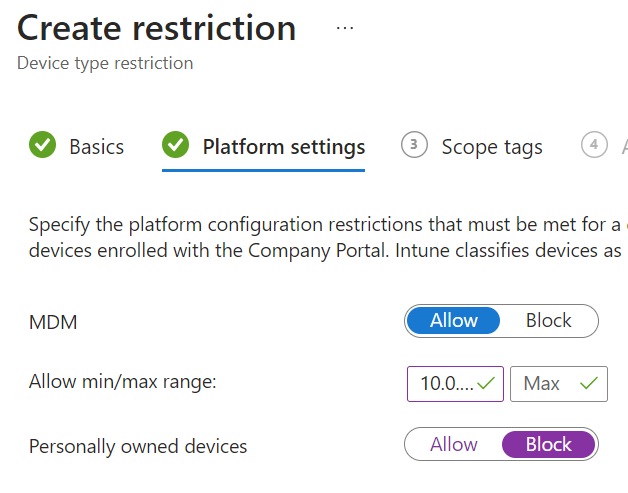
Click Next, assign the policy, and click Next and Create.

When a device tries to enroll with a Windows version lower than 19044 or a Personal owned, the user is not allowed to do so. If the device hits this policy, we can see this under the event viewer in DeviceManagement-Enterprise-Diagnostics-Provider with an error 71

Creating policies for Windows 10 and Windows 11 involves a two-step process. First, you must create two separate policies for each operating system. Next, you must filter these policies to include the specific Windows version. By filtering policies, you can ensure that the right configurations are applied to the right devices, depending on their specific operating system. This helps to prevent any potential issues that may arise from applying the wrong configurations to the wrong devices.
Windows 10
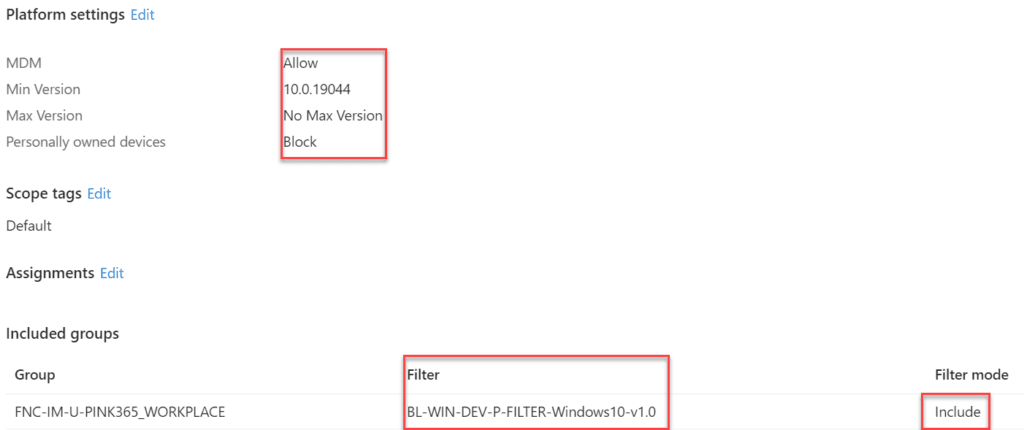
Windows 11

Default platform restriction
In the platform restrictions, a default policy allows personal and corporate devices to enroll in our organization. We can disable both so that only the just-created policies will take effect. When using Windows 365 CloudPC, there is a need only to allow MDM, but we can restrict it more with a minimal OS version.

Enrollment device limit restrictions
Enrollment device limit restrictions are essential in hardening Intune MDM because they allow you to control the number of devices enrolled in your organization’s Intune solution. By setting device enrollment limits, you can ensure that only authorized devices are enrolled in the Intune service and that your organization’s resources are not overloaded with unnecessary devices. This can help prevent security breaches and data loss and ensure your organization’s devices are properly managed and secured.
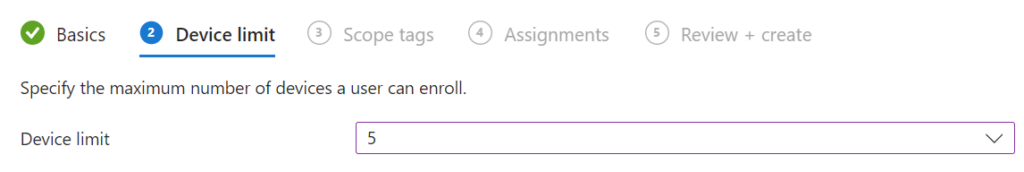
We like to set device restrictions of a maximum of 5 devices. It allows for better management of enrolled devices, which can help ensure they are properly updated and secured according to your organization’s policies.
To set the device enrollment restrictions, we must go to Devices | Enrollment | Enrollment device limit restrictions, click on + Create restriction, fill in a name and description, and click Next. Set the maximum number of devices a user can enroll where we like to set it to 5.
Set these platform and device enrollment restrictions in Entra
However, to ensure that your organization’s devices and data are fully protected, applying these restrictions in your Entra AD (Active Directory) environment is important.
This makes it easier to apply security policies consistently across all devices and ensure that your organization’s data is protected. To implement the platform restrictions and device limit restrictions in Entra AD we have to go to https://entra.microsoft.com/, go to Devices | Device settings, and make the settings below for the group use the same as we did in Intune

Deployment profile
An Intune deployment profile helps organizations creating Intune deployment profile helps organizations streamline device management and improve security. If we want to harden deployment profiles, we like to target it to a specific group and not to all devices and adjust the setting

If we select Yes, it will register all targeted devices to Autopilot if they are not already registered. The next time registered devices go through the Windows Out of Box Experience (OOBE), they will go through the assigned Autopilot scenario. So that’s why we want it to be set to No and a specific group.
Requiring MFA for device join
Requiring Multi-Factor Authentication (MFA) for device join is a security measure that can help enhance MDM hardening in Intune. By enabling this feature, all devices that attempt to join your organization’s network will be required to provide a second form of authentication in addition to their password. With MFA, your organization can ensure that only trusted devices and users can access corporate resources, which can help protect your business from potential security threats.
For this to work, we need to create a conditional access policy set to all users (don’t forget to exclude the Breakglass account group), And at the target resources, set a user action Register or Join devices

with a Grant Require multifactor authentication

Stop looking for a great Conditional access baseline and go to Kenneth van Surksum’s baseline.
Conclusion
We showed various aspects of MDM hardening using Microsoft Intune. It covers the importance of MDM hardening, the device enrollment process, and specific settings that can enhance security, such as automatic MDM enrollment, device platform restrictions, and enrollment device limit restrictions. The article also explains how to apply these settings in Microsoft Entra and the role of Intune deployment profiles. Additionally, it highlights the necessity of requiring Multi-Factor Authentication (MFA).
