Autopilot device preparation simplifies setting up and configuring devices for your organization. This new feature from Microsoft streamlines the deployment of devices and ensures that they are properly configured for use within your organization. With Autopilot device preparation, IT administrators can automate the setup process, saving time and reducing potential errors. This new edition of Autopilot is expected to bring greater efficiency and convenience to device deployment processes.
Current Autopilot
Autopilot device preparation will overhaul the way we approach device enrollment. The current autopilot feature works with the dynamic device group, a deployment profile, and a separate Enrollment Status page. The dynamic device group allows for easy and efficient organization of devices based on specific criteria, while the separate ESP page provides a dedicated space for managing autopilot configurations. This setup ensures that autopilot can effectively deploy and manage devices with minimal manual intervention, streamlining the process and enhancing overall efficiency.
Autopilot Device preparation
Autopilot device preparation is built next to Autopilot to allow running next to each other without causing any issues in our production environments. With the new Autopilot experience, there is no need to upload hardware hashes; there is a new way to only allow corporate devices in our environment, which we will cover in a separate blog post. To compare the new with the older Autopilot Rudy Ooms made a nice picture. to show the difference. With the new Autopilot experience, IT administrators can automate the setup process, saving time and reducing potential errors. This new edition of Autopilot is expected to bring greater efficiency and convenience to device deployment processes.
There are two possible device ownership options we can take with autopilot device preparation: personal and corporate. If we need to enable this for personal devices so it becomes a corporate device, we should enable this in the platform restrictions. To onboard corporate devices, we no longer need to upload hardware hashes; we need to use corporate identifiers released simultaneously as device preparation. A separate blog about Corporate Identifiers can be found here
In the next chapter, we will go into how to prepare everything.
Requirements
- A user security group
- A device security group with a particular owner
- Apps targeted to the device group
- Specific policies targeted to devices
- Device preparation policy
- Check MDM settings (allow personal)
In the following items, we will only discuss the parts that need extra explanation (apps and policies are not covered). The user security group is where we will target our device preparation policy; this is just a normal security group we can use; in our case, we will use a Device Preparation Ring 1. The device security group will need an owner set; the device group will be used to add our devices and isn’t a dynamic group.
Create a device security group
We just need to create a normal security group to create the device security group. In our case, we will use MEM-DY-WIN-D-Autopilot Device Preparation Ring 1-P. We will add a service principle as the owner to this group.
Go to Intune | Groups and create the group under owners click on + Add owners, search for Intune Provisioning Client, and Select it
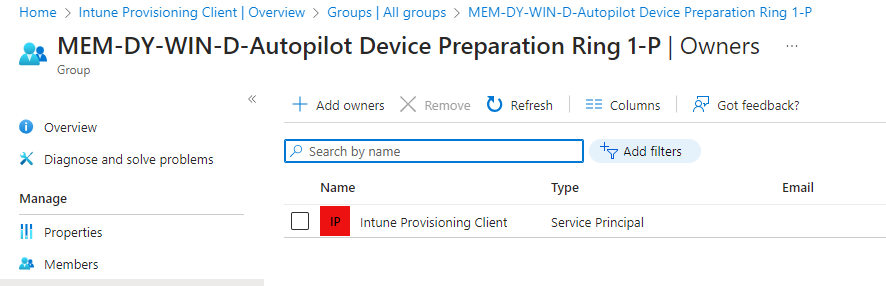
If the service principle is not available in the tenant we need to add it with a PowerShell script
|
1 2 3 |
import-module AzureAD Connect-AzureAD New-AzureADServicePrincipal -AppId f1346770-5b25-470b-88bd-d5744ab7952c |
Creating a Device preparation policy
Now that we are coming to the fun part, we can create our new policy to use the new autopilot experience’s new profile. Therefore fore we need to go to the new part of Intune just released under Devices | Enrollment and click Device preparation policies
Here we will click on + Create
Click on Next and fill in a name for the policy
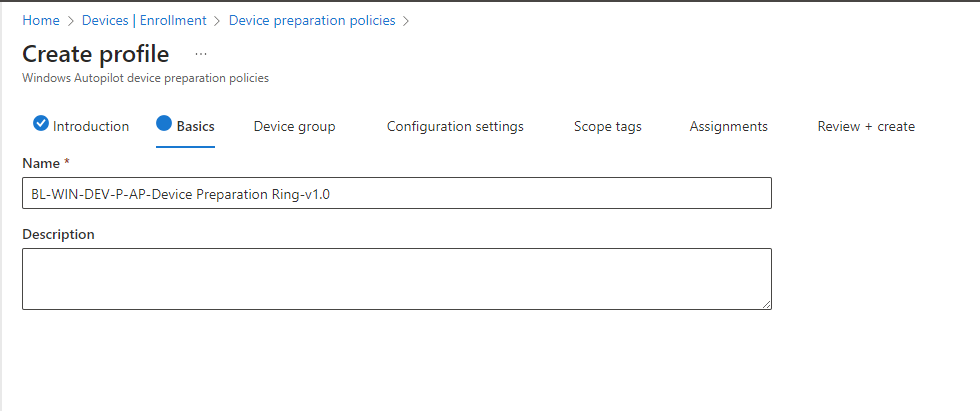
Click Next, here we will enter the previously created Device Group in the search field with the added owner, add it, and click Next
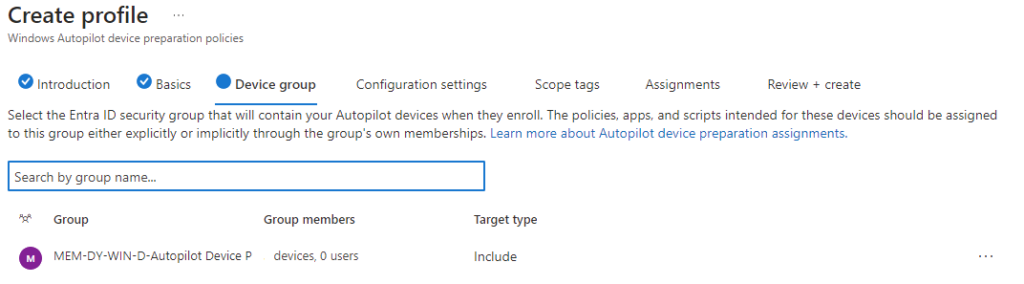
now we will come to the fully new experience where all the things come together
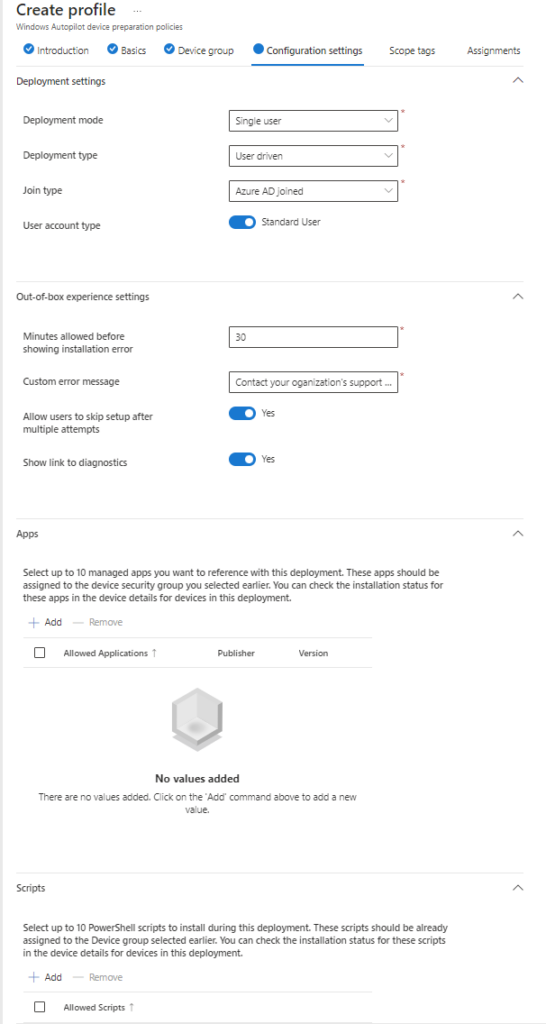
Here, we will add some applications we would like to install in the autopilot phase; further, we will leave it as-is in our situation. and click Next. click Next after you fill in the scope tags u want to use.
In the Assignment search field, search for the user group we created. This will be one of the changes with the new experience there. We targeted it to a dynamic device group and are now targeting it to a user. Now, review and create the policy.
Devices monitoring reports
There is a new enrollment monitoring report which can be found under Devices | Monitor and then go to Windows Autopilot device preparation deployments
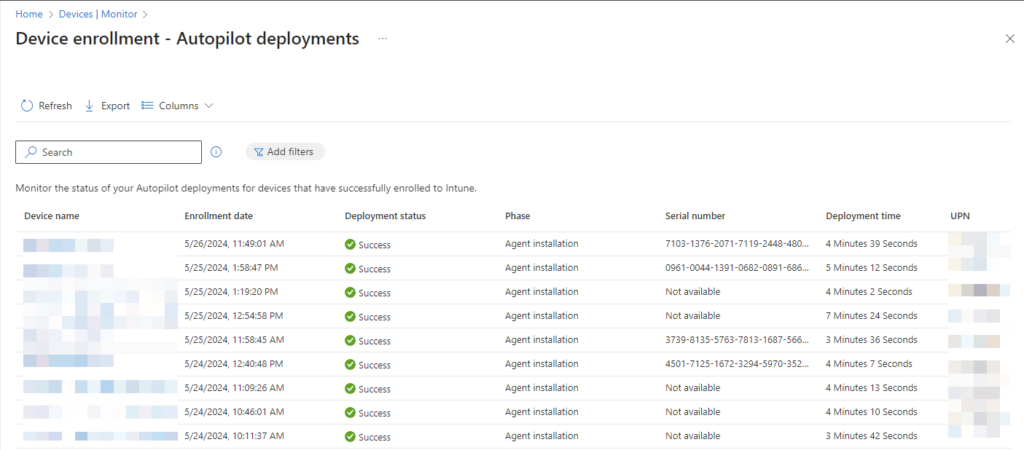
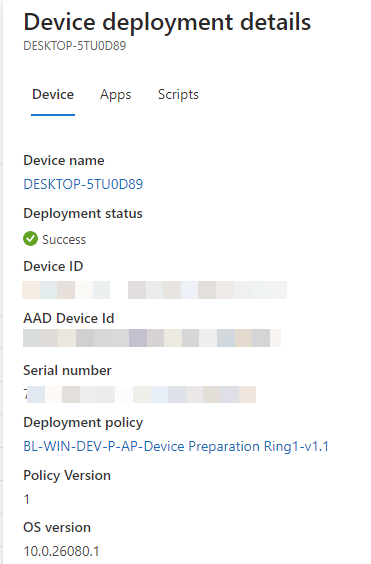
When clicking on a device name we will see the deployment details, some extra details are shown which would make it much easier to troubleshoot like Device name, Deployment Status, Deployment policy, Apps installed, and scripts
User experience
After signing in with the user who is a member of the user security group( in our case Device Preparation Ring 1) it will look like this (speed up this one took about 5 minutes)
Conclusion
Based on the details highlighted in the blog post, preparing the new Autopilot Device significantly improves deployment creation. The streamlined approach provides a much better user experience during the autopilot phase, resulting in faster operations. These enhancements will positively impact efficiency and productivity within our deployment processes. With the implementation of the new Autopilot Device preparation, we anticipate a smoother and more streamlined workflow. This will be a promising new feature; let’s pay attention to where this will lead us.

[…] identifiers are another piece of the puzzle. Following the introduction of Autopilot Device preparation, it’s important to enhance security by restricting the addition of only allowing […]