Many customers still want to use Google Chrome as there default browser because there users are known with the usage of Chrome. We are offering a standard security for Edge and wanted to create a security baseline for Chrome.
Because the settings catalog is general available, It is good to have a look at all the settings we can set for Google Chrome or the settings which are not available (yet). Because there is a Edge Baseline available in Microsoft Endpoint Manager and we are using this as a base security layer for Edge this would be nice to try and create this for Google Chrome as well.
Which setting are set/available in the Edge Baseline
- Supported authentication schemes
Baseline default: Enabled- Supported authentication schemes
Baseline defaults: Two items: NTLM and Negotiate
- Supported authentication schemes
- Default Adobe Flash setting
Baseline default: Enabled- Default Adobe Flash setting
Baseline default: Block the Adobe Flash plugin
- Default Adobe Flash setting
- Control which extensions cannot be installed
Baseline default: Enabled- Extension IDs the user should be prevented from installing (or * for all)
Baseline default: Not configured by default. Manually add one or more Extension IDs
- Extension IDs the user should be prevented from installing (or * for all)
- Allow user-level native messaging hosts (installed without admin permissions)
Baseline default: Disabled - Enable saving passwords to the password manager
Baseline default: Disabled - Prevent bypassing Microsoft Defender SmartScreen prompts for sites
Baseline default: Enabled - Prevent bypassing of Microsoft Defender SmartScreen warnings about downloads
Baseline default: Enabled - Enable site isolation for every site
Baseline default: EnabledMicrosoft Edge also supports IsolateOrigens policy that can isolate additional, finer-grained origins. Intune doesn’t support configuring the IsolateOrigins policy. - Configure Microsoft Defender SmartScreen
Baseline default: Enabled
This policy is available only on Windows instances that are joined to a Microsoft Active Director domain, or on Windows 10/11 Pro or Enterprise instances that are enrolled for device management. - Configure Microsoft Defender SmartScreen to block potentially unwanted apps
Baseline default: EnabledThis policy is available only on Windows instances that are joined to a Microsoft Active Director domain, or on Windows 10/11 Pro or Enterprise instances that are enrolled for device management. - Allow users to proceed from the SSL warning page
Baseline default: Disabled - Minimum SSL version enabled
Baseline default: Enabled- Minimum SSL version enabled
Baseline default: TLS 1.2
- Minimum SSL version enabled
Edge vs Chrome settings (Settings Catalog)
When searching in the settings catalog and comparing the items in the Edge baseline and what is available for chrome there where a lot of settings there to set:
Found:
- Supported authentication schemes (same name)
- Default Adobe Flash setting (There is a setting but placed in Removed policies)
- Control which extensions cannot be installed (Configure extension installation blocklist)
- Allow user-level native messaging hosts (same name)
- Enable saving passwords to the password manager (same name)
- Prevent bypassing Microsoft Defender SmartScreen prompts for sites (not there)
- Prevent bypassing of Microsoft Defender SmartScreen warnings about downloads (not there)
- Enable site isolation for every site (Enable Site Isolation for specified origins)
- Allow users to proceed from the SSL warning page (Allow proceeding from the SSL warning page)
- Minimum SSL version enabled (same name)
Create Setting Catalog policy
Click Next
Get all the settings in a listed above in the Edge vs Chrome settings with the settings from the baseline in it.
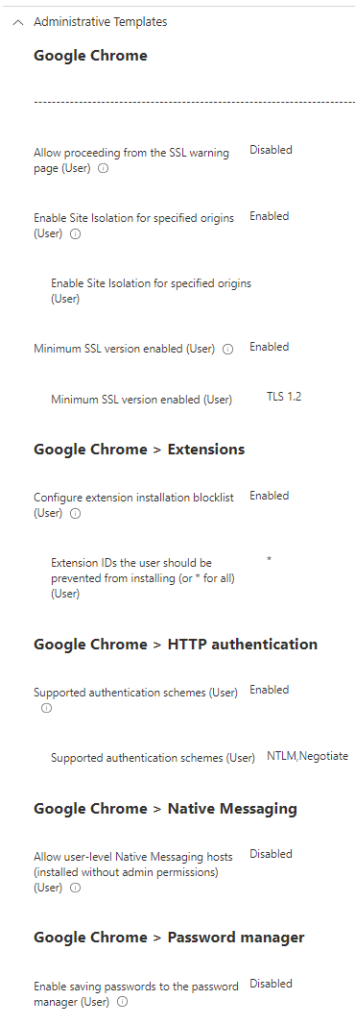
Policy in JSON for importing
I have created the policy and exported it. so you can import it to the tenant for testing purposes before heading over to production. You can download it at Github or copy paste to a file
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 |
{ "$description": "", "assignments": [], "platforms": "windows10", "settings": [ { "settingInstance": { "@odata.type": "#microsoft.graph.deviceManagementConfigurationChoiceSettingInstance", "choiceSettingValue": { "children": [ { "@odata.type": "#microsoft.graph.deviceManagementConfigurationChoiceSettingInstance", "choiceSettingValue": { "children": [], "settingValueTemplateReference": null, "value": "user_vendor_msft_policy_config_chromeintunev1~policy~googlechrome_sslversionmin_sslversionmin_tls1.2" }, "settingDefinitionId": "user_vendor_msft_policy_config_chromeintunev1~policy~googlechrome_sslversionmin_sslversionmin", "settingInstanceTemplateReference": null } ], "settingValueTemplateReference": null, "value": "user_vendor_msft_policy_config_chromeintunev1~policy~googlechrome_sslversionmin_1" }, "settingDefinitionId": "user_vendor_msft_policy_config_chromeintunev1~policy~googlechrome_sslversionmin", "settingInstanceTemplateReference": null } }, { "settingInstance": { "@odata.type": "#microsoft.graph.deviceManagementConfigurationChoiceSettingInstance", "choiceSettingValue": { "children": [ { "@odata.type": "#microsoft.graph.deviceManagementConfigurationSimpleSettingCollectionInstance", "settingDefinitionId": "user_vendor_msft_policy_config_chromeintunev1~policy~googlechrome~extensions_extensioninstallblocklist_extensioninstallblocklistdesc", "settingInstanceTemplateReference": null, "simpleSettingCollectionValue": [ { "@odata.type": "#microsoft.graph.deviceManagementConfigurationStringSettingValue", "settingValueTemplateReference": null, "value": "*" } ] } ], "settingValueTemplateReference": null, "value": "user_vendor_msft_policy_config_chromeintunev1~policy~googlechrome~extensions_extensioninstallblocklist_1" }, "settingDefinitionId": "user_vendor_msft_policy_config_chromeintunev1~policy~googlechrome~extensions_extensioninstallblocklist", "settingInstanceTemplateReference": null } }, { "settingInstance": { "@odata.type": "#microsoft.graph.deviceManagementConfigurationChoiceSettingInstance", "choiceSettingValue": { "children": [ { "@odata.type": "#microsoft.graph.deviceManagementConfigurationSimpleSettingInstance", "settingDefinitionId": "user_vendor_msft_policy_config_chromeintunev1~policy~googlechrome_isolateorigins_isolateorigins", "settingInstanceTemplateReference": null, "simpleSettingValue": { "@odata.type": "#microsoft.graph.deviceManagementConfigurationStringSettingValue", "settingValueTemplateReference": null, "value": "" } } ], "settingValueTemplateReference": null, "value": "user_vendor_msft_policy_config_chromeintunev1~policy~googlechrome_isolateorigins_1" }, "settingDefinitionId": "user_vendor_msft_policy_config_chromeintunev1~policy~googlechrome_isolateorigins", "settingInstanceTemplateReference": null } }, { "settingInstance": { "@odata.type": "#microsoft.graph.deviceManagementConfigurationChoiceSettingInstance", "choiceSettingValue": { "children": [ { "@odata.type": "#microsoft.graph.deviceManagementConfigurationSimpleSettingInstance", "settingDefinitionId": "user_vendor_msft_policy_config_chromeintunev1~policy~googlechrome~httpauthentication_authschemes_authschemes", "settingInstanceTemplateReference": null, "simpleSettingValue": { "@odata.type": "#microsoft.graph.deviceManagementConfigurationStringSettingValue", "settingValueTemplateReference": null, "value": "NTLM,Negotiate" } } ], "settingValueTemplateReference": null, "value": "user_vendor_msft_policy_config_chromeintunev1~policy~googlechrome~httpauthentication_authschemes_1" }, "settingDefinitionId": "user_vendor_msft_policy_config_chromeintunev1~policy~googlechrome~httpauthentication_authschemes", "settingInstanceTemplateReference": null } }, { "settingInstance": { "@odata.type": "#microsoft.graph.deviceManagementConfigurationChoiceSettingInstance", "choiceSettingValue": { "children": [], "settingValueTemplateReference": null, "value": "user_vendor_msft_policy_config_chromeintunev1~policy~googlechrome_sslerroroverrideallowed_0" }, "settingDefinitionId": "user_vendor_msft_policy_config_chromeintunev1~policy~googlechrome_sslerroroverrideallowed", "settingInstanceTemplateReference": null } }, { "settingInstance": { "@odata.type": "#microsoft.graph.deviceManagementConfigurationChoiceSettingInstance", "choiceSettingValue": { "children": [], "settingValueTemplateReference": null, "value": "user_vendor_msft_policy_config_chromeintunev1~policy~googlechrome~nativemessaging_nativemessaginguserlevelhosts_0" }, "settingDefinitionId": "user_vendor_msft_policy_config_chromeintunev1~policy~googlechrome~nativemessaging_nativemessaginguserlevelhosts", "settingInstanceTemplateReference": null } }, { "settingInstance": { "@odata.type": "#microsoft.graph.deviceManagementConfigurationChoiceSettingInstance", "choiceSettingValue": { "children": [], "settingValueTemplateReference": null, "value": "user_vendor_msft_policy_config_chromeintunev1~policy~googlechrome~passwordmanager_passwordmanagerenabled_0" }, "settingDefinitionId": "user_vendor_msft_policy_config_chromeintunev1~policy~googlechrome~passwordmanager_passwordmanagerenabled", "settingInstanceTemplateReference": null } } ], "technologies": "mdm", "templateReference": { "templateFamily": "none", "templateId": "" } } |
Conclusion
Because there are still people using chrome and not the Edge Browser I wanted to create a security baseline just like we use for Edge. For what I have seen it possible to recreate a big portion of the policy set except the Defender part.
Maybe it is good to have a good conversation about why to use Edge above Chrome because of the possibility to use Defender SmartScreen options and many other features.

[…] Create the Chrome baseline via Settings Catalog […]
[…] are using Microsoft Security Baseline for Edge (and Chrome) because it includes the best practices and recommendations on settings that impact security. […]