Last week I had to troubleshoot a problem with a customer, where they wanted to reset a user’s PIN but were getting an error. After some digging, I found the problem and made two specific changes to their environment.
PIN reset error
There was a user trying to reset his/her PIN of the device but was getting an error “Something went wrong with error code CAA20004”
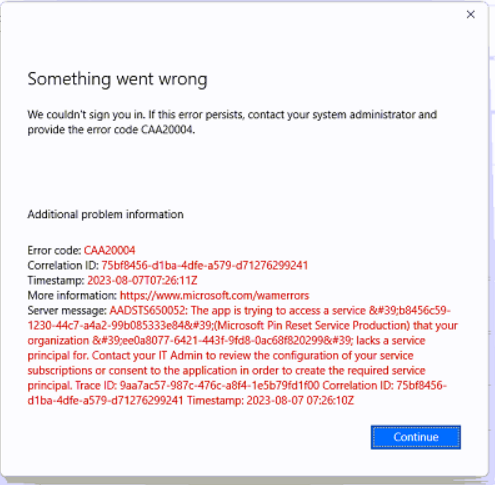
The first step was easy to check if there was a policy in place, this was the case with an OMA URI, and this is something we wanted to update to our baseline configuration. Herefore, we introduced a setting catalog policy which we will create and show later. Because the PIN reset was enabled on the device it wants to use the Non-destructive PIN reset, which keeps the Windows Hello for Business container and keys on the device and only resets the authorization key PIN of the user.
The next step was why the user got an error after trying to reset the device’s PIN. After looking into the tenant of the customer I found the problem and because this one is easy to forget I wanted to create a short blog about it.
Create a reset policy
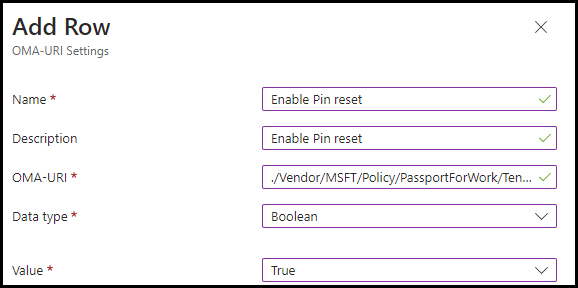
Before the settings catalog, we needed to create a Custom OMA-URI to enable PIN reset possibility on the user’s device which was created
OMA-URI: ./Vendor/MSFT/Policy/PassportForWork/TenantId/Policies/EnablePinRecoveryData type: Boolean Value: True. The TenantID value can be found in Azure Active directory properties.
But we like to use the settings catalog and create a policy for Windows Hello for Business and the PIN reset in one policy. Because we don’t want to set the Windows Hello for Business into the tenant-wide policy we create a separate one to control which devices are getting or are allowed to use Windows Hello for Business.
There we have to create a new policy. Go to Devices | Windows | Configuration profiles and click + Create profile. Select platform Windows 10 and later and profile type Settings Catalog click Create
Fill in a name and description to match you’re naming convention and click Next. Click on + Add settings and fill in the settings below. These settings are the same as the Security baseline by Microsoft which incorporates the best practices in security and productivity, and we added some extra to enable the PIN reset.
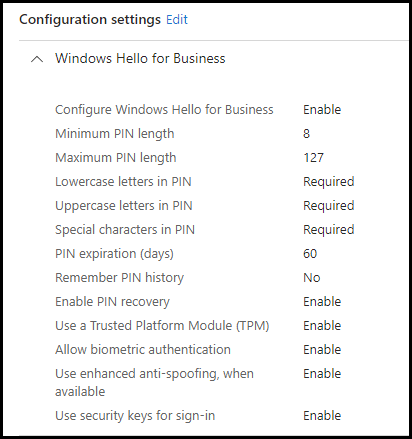
Save the policy after you assigned it, and the testing of the policy can begin.
Enable the PIN reset service
If we are using the Non-destructive PIN method we need to enable this service tenant-wide. Herefore, we need to register two applications in Azure to get this working.
Microsoft Pin Reset Service Production application
The first application we need to enable is Microsoft Pin Reset Service Production, open a browser and sign in with your Global Admin credentials on Azure, open a new tab, and paste in the following URL of the first application https://login.windows.net/common/oauth2/authorize?response_type=code&client_id=b8456c59-1230-44c7-a4a2-99b085333e84&redirect_uri=https%3A%2F%2Fcred.microsoft.com&prompt=admin_consent
The following page will be shown
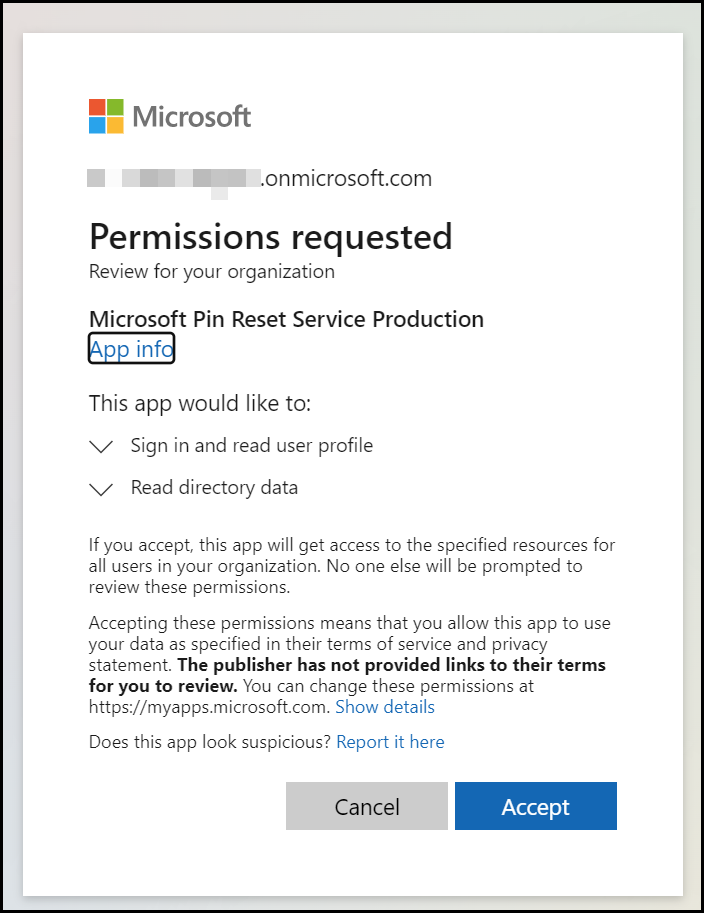
Click on Accept. The next page will show the following

The first application we need to enable is Microsoft Pin Reset Client Production, open a new tab, and paste in the following URL of the second application we need to accept https://login.windows.net/common/oauth2/authorize?response_type=code&client_id=9115dd05-fad5-4f9c-acc7-305d08b1b04e&prompt=admin_consent
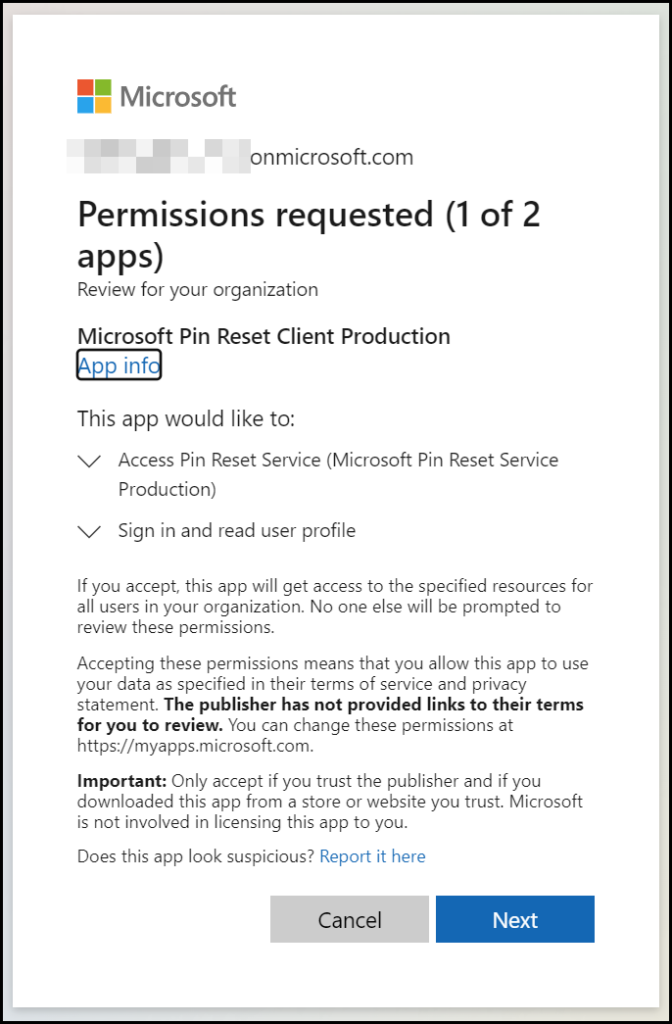
Click Next
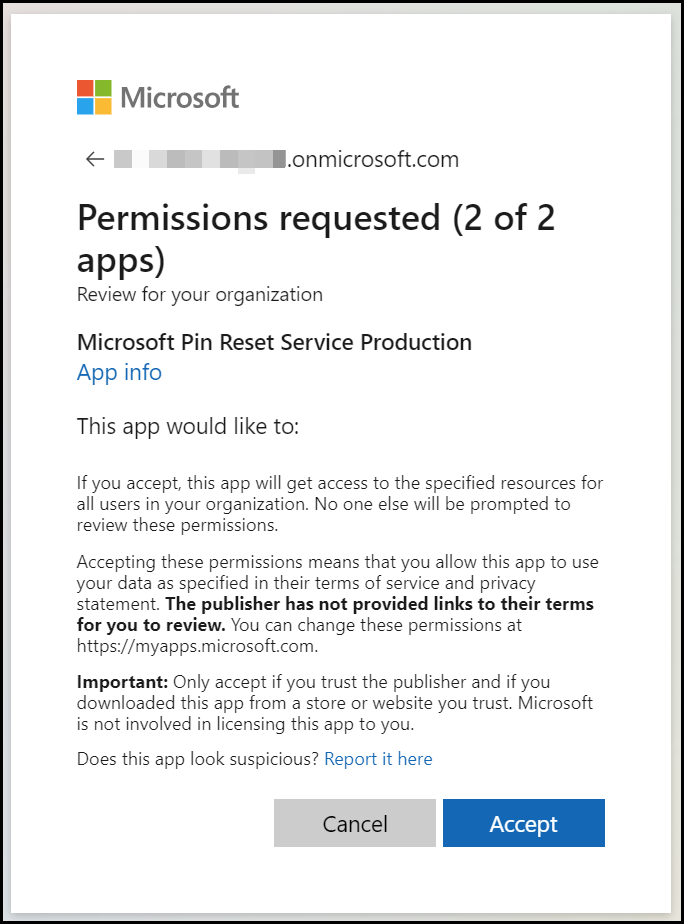
Click on Accept
This sometimes takes a long time or looks like it is hanging on a process. (you can close the Tab after some minutes) After several minutes you can check if both applications are being accepted in your environment by looking at the enterprise applications in Azure Active Directory or Entra of course.
Search for Microsoft PIN
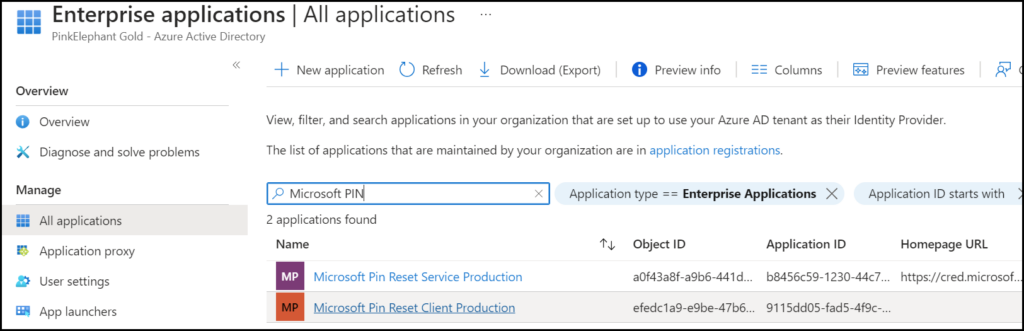
Now users are able to reset the PIN.
Conclusion
What we have found is an easy step to forget in the setup of the modern workplace, thankfully it is easy to make the change it will be working for our user. I wish the error would tell a little bit more and it would be great if these applications do not need to be enabled. But for now, it is what it is.

[…] Enable PIN reset […]