For our devices, we want to have a good solution for updating a driver. Microsoft just released generally available driver updates for Windows, which is built on the Windows Update for Business deployment service. It will give us intelligent servicing, optional drivers, firmware update management, and detailed reporting.
Prerequisites driver updates
Before we can create our first policy to set up the driver updates via Intune we have to check if we have the right prerequisites.
License needed for driver updates
- Windows 10/11 Enterprise E3 or E5 (included in Microsoft 365 F3, E3, or E5)
- Windows 10/11 Education A3 or A5 (included in Microsoft 365 A3 or A5)
- Windows Virtual Desktop Access E3 or E5
- Microsoft 365 Business Premium
- Intune plan 1
- Azure AD Free or Higher
Operating System requirement
Windows 10 or Windows 11 Pro, Enterprise, Education
Telemetry and Windows diagnostics
For telemetry the minimal value required is needed, if you already enabled (I hope so) the Windows Update for Business reports the right telemetry setting is already in place, otherwise we have to create a policy which can be done via a device restriction or a settings catalog policy
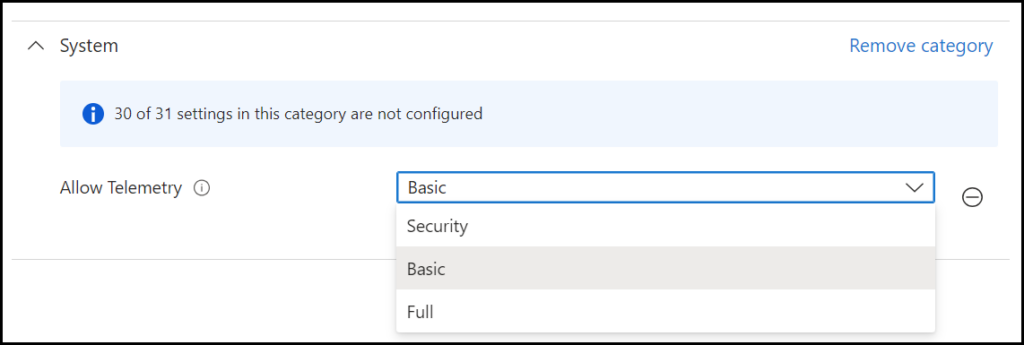
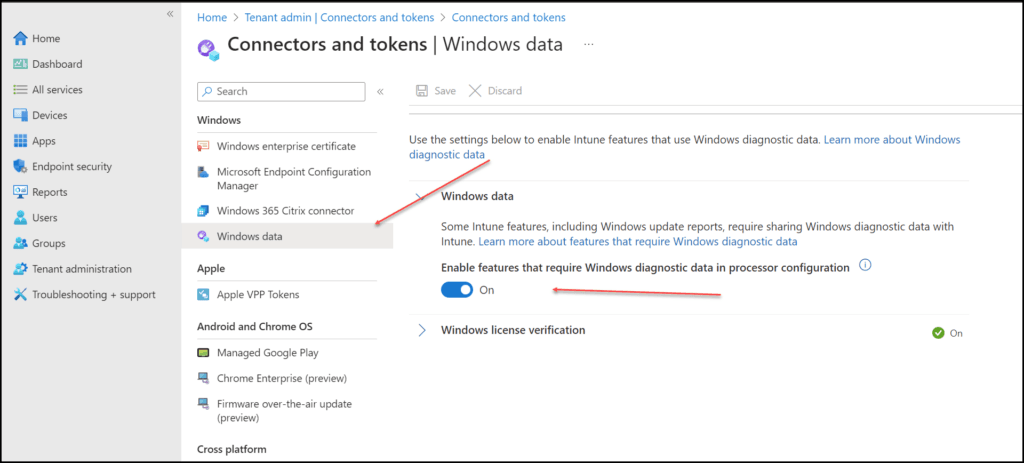
To check if the Windows diagnostics settings are in place. For this, we must go to Tenant administration | Connectors and tokens | Windows data, Set Windows diagnostics data to On.
Windows Driver Updates
With driver updates, we have two possible settings manual and automatic. Where the option manual needs manual approval of drivers and select the day to start offering the update when you approve them. With this option, no drivers are offered until manually approved. Automatic updates will be automatically approved, with the option to set how long it will wait until the driver is offered to a device.
Automatic is a great way to use deployment rings because we really like that, this is the approach we will use also because it will only approve the recommended drivers.
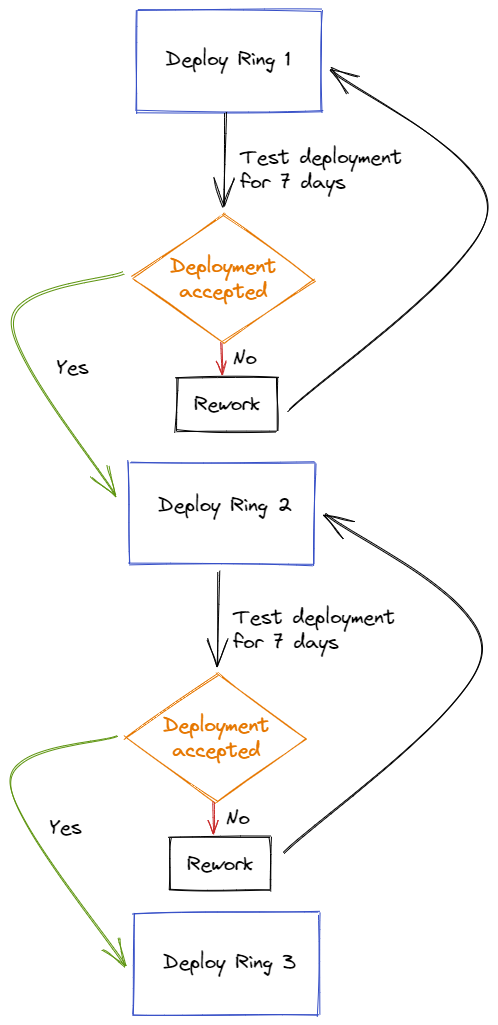
Deployment ring concept
Within the Modern Workplace environments, we provide to our customers, we have the concept of Deployment Rings. These deployment rings define the order in which we will deploy updates or policies to the environment. Currently, 3 deployment rings are determined to get a DTP process. Because we use an assignment of policies to users only, take in mind that these deployment rings can be created with device groups as well.
• Deployment Ring 1, everyone with an IT-related function
• Deployment Ring 2, a representative set of end users working within the business
• Deployment Ring 3 (contains everyone)
We like to use standard deployment rings with specific release moments:
- Deployment Ring 1 receives the deployment immediately.
- Deployment Ring 2 receives the deployment after 7 days, only when Ring 1 accepts it.
- Deployment Ring 3 receives the deployment after 14 days, only when Ring 2 accepts it.
To use this concept create 3 security groups: Ring1, Ring2, and Ring3 (where every user is a member of Ring3). It is also possible to create more rings to you’re liking.
The architecture of driver updates
To create a better feeling about how everything is going to work I used the architectural picture of Microsoft .
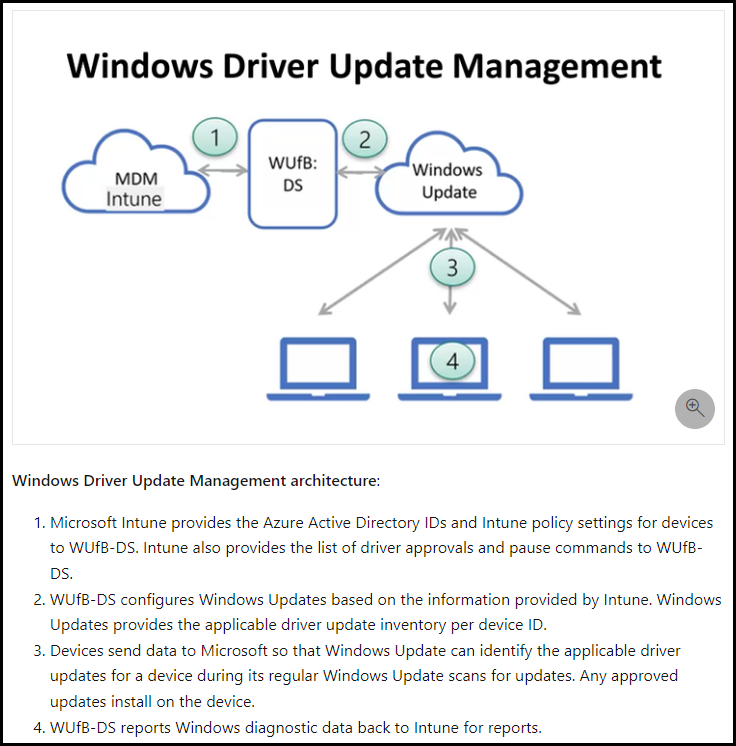
Devices sync with the WUfB-DS service each day when the device runs a Windows Update scan.
Create policy
We are going to create 3 policies in our situation. For every deployment ring, we will create a different policy that will make updates available after different days.
To create the policy go to Devices | Driver updates for Windows 10 and later click on + Create profile
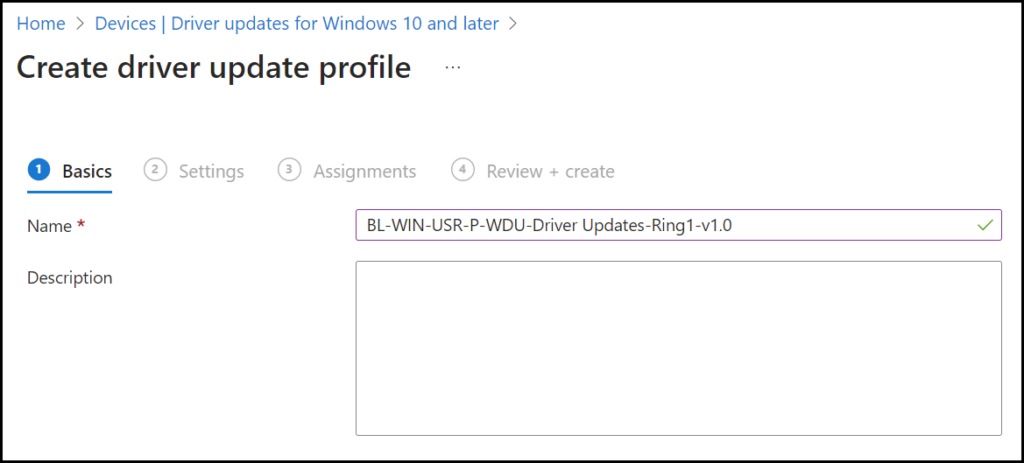
Fill in a Name and click Next.
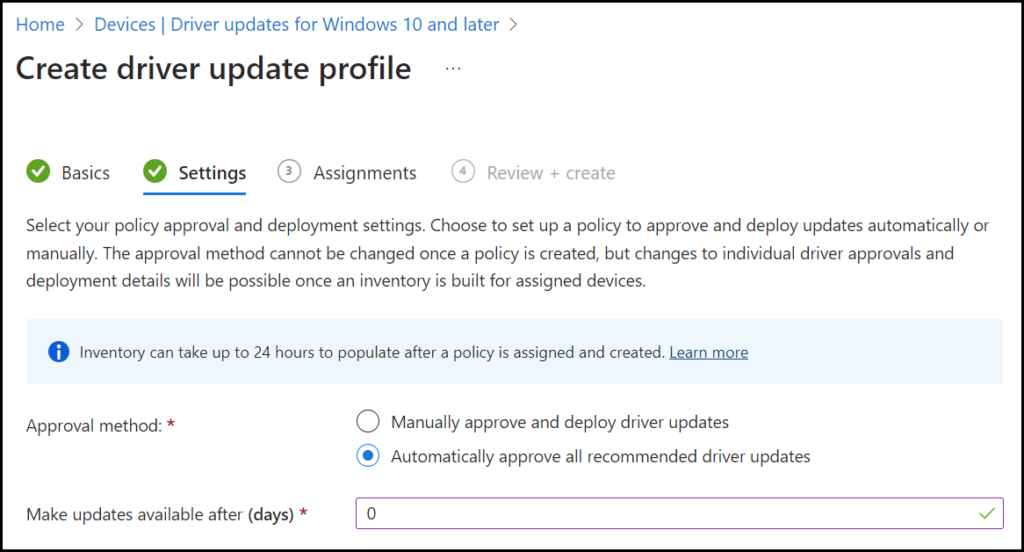
Set the approval method to Automatically approve all recommended driver updates and fill in the Make updates available after (days) for this we will use the following:
- Ring 1 will get it after 0 days because we want to deliver these updates as fast as possible to them.
- Ring 2 will get it after 7 days, then Ring 1 finished testing it.
- Ring 3 will get it after 14 days.
Click Next and assign the Ring 1 User group.
Take note: Inventory can take up to 24 hours to populate after a policy is assigned and created.
Driver blade
After creating the policy, and the inventory is run we can see what is happening in the driver blade en where to do what. If we go back to Devices | Driver updates for Windows 10 and later we can see the policy we created
Automatic:

Manual:

Manual approval
For manual approval of drivers, we will have to click on Drivers to review. Here we can see two specific tabs Recommended drivers and Other drivers.
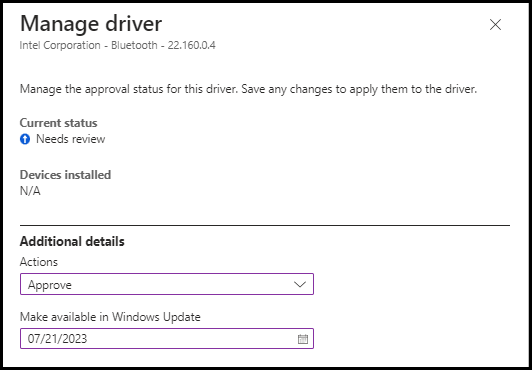
Under Recommended drivers, we can see a list of drivers available for the devices. To install a driver to a device we need to review it driver by driver. Click on the driver which needs the review (These steps can be also used for Other Drivers)
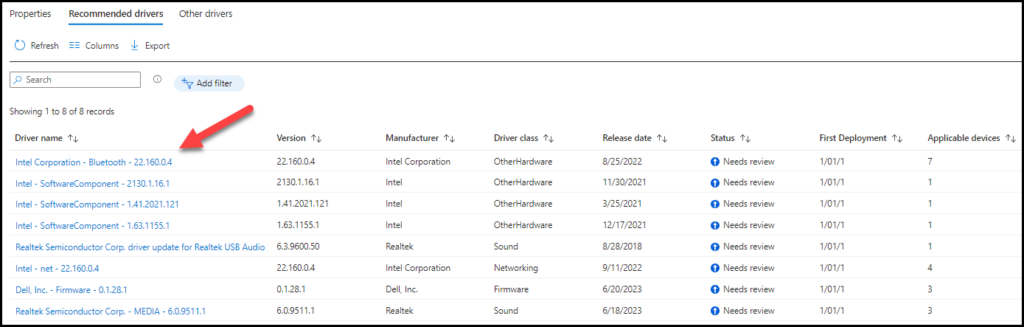
Click on the action field to approve it
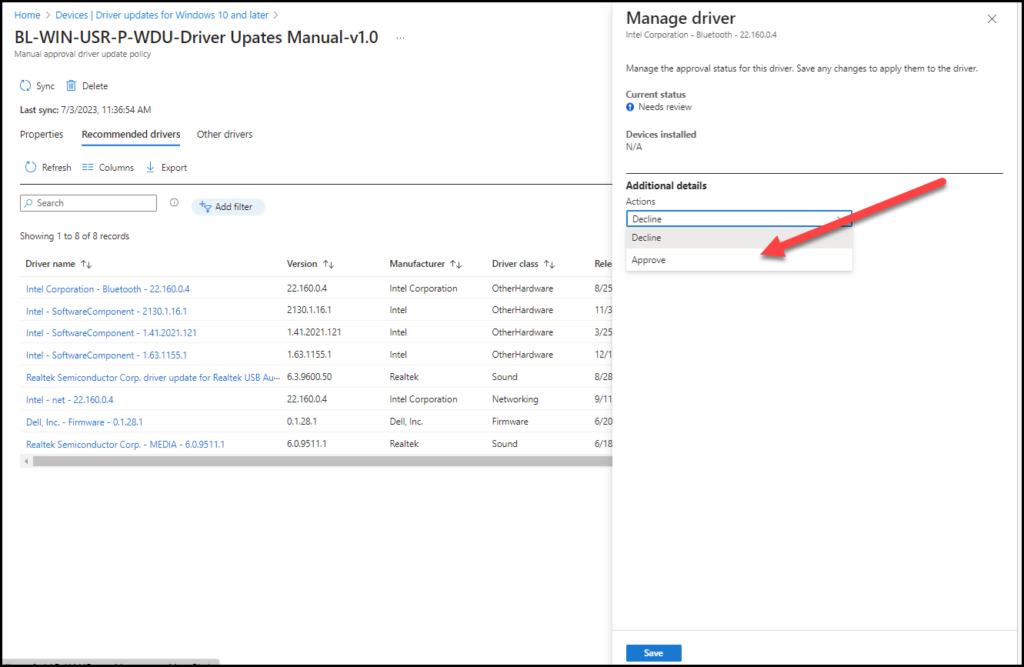
Choose a date to make it available in Windows Update and click Save
Automatic approvals
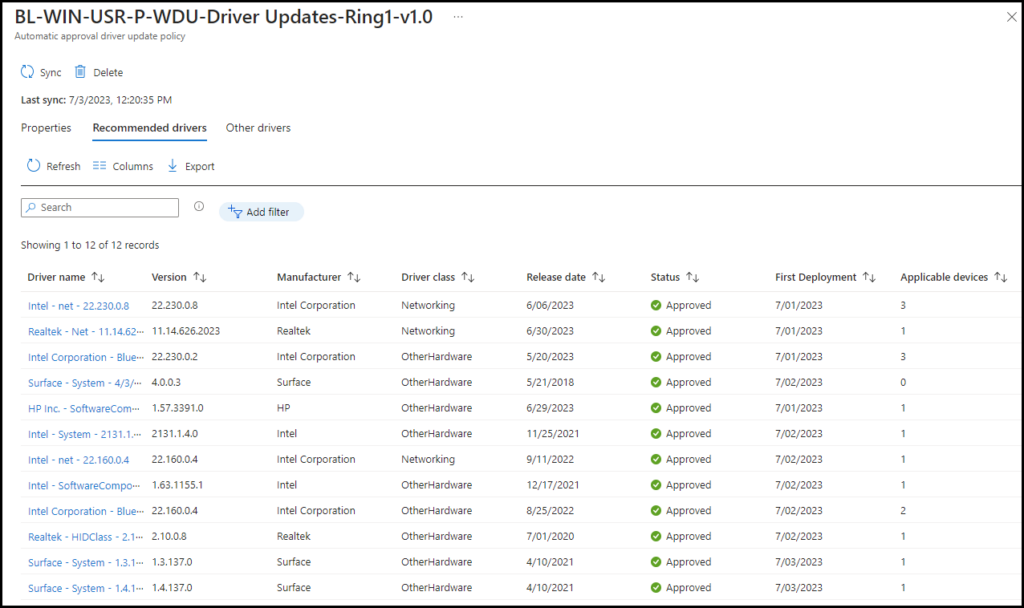
For automatic approval of drivers, Microsoft will take care of approving the recommended drivers, and manually we can review the Other drivers tab
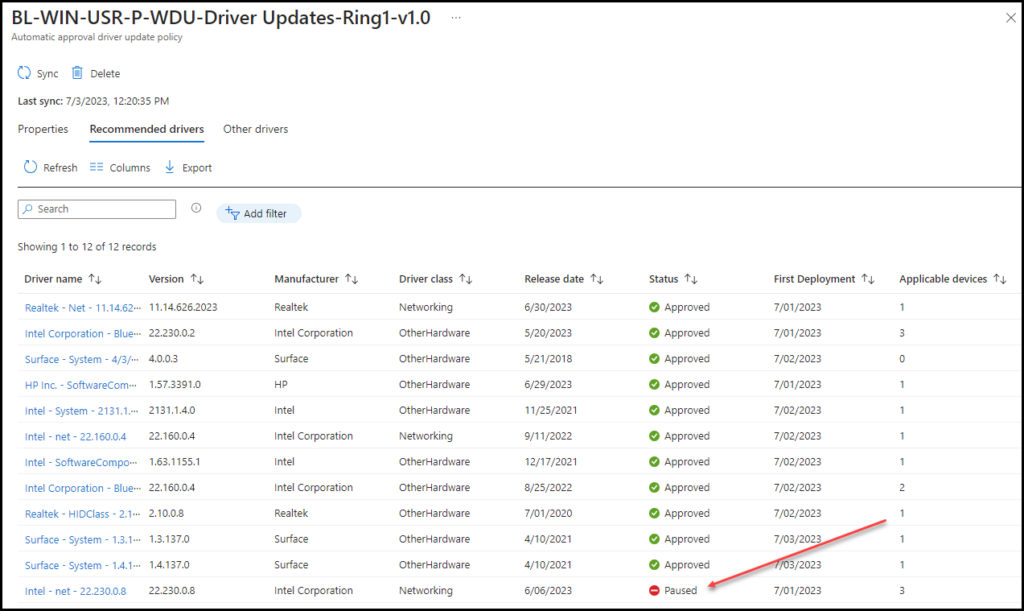
Under Recommended drivers, we can see a list of drivers available for the devices. These drivers are already been approved by Microsoft.
If we click on the Driver we can see the following
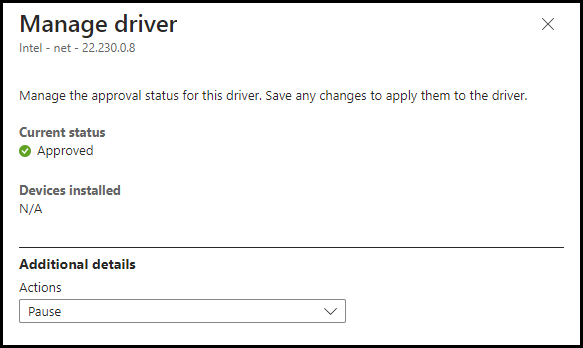
So these updates are being approved automatically and made available via Windows Updates
Pausing driver updates
If a driver fails in ring 1 or ring 2 and is causing issues you do not want to install these to the rest of you’re devices (in our case ring 3 users), therefore you need to pause the specific driver to install
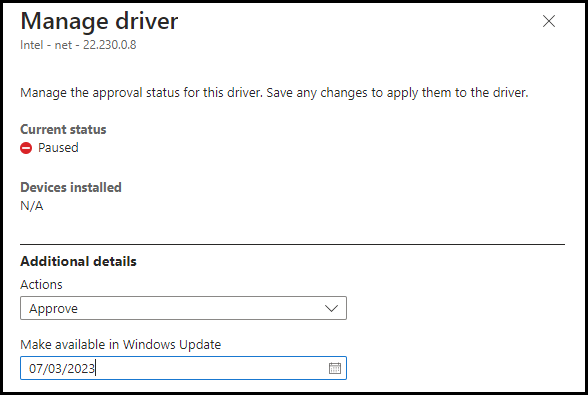
Go to the policy which handles the drivers updates, the same approach is for manual and automatic policies. Click on the driver name and there you will see under Additional details that actions are on Pause and now we only need to Save it.
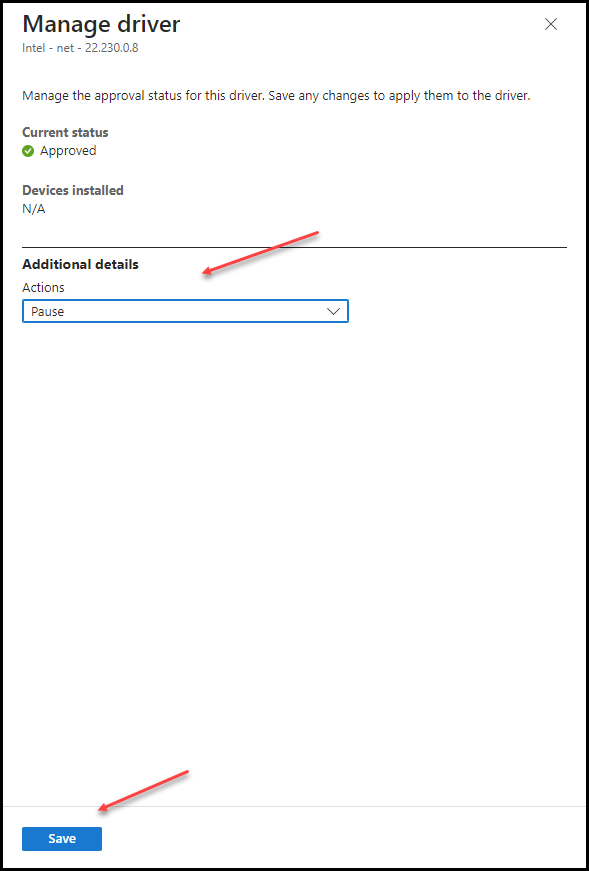
After saving it the blade will look like this
Maybe after troubleshooting you need to approve the driver again. just do this by clicking the driver and approving it again, choose a data to make it available, and click on Save
Conclusion
Driver and firmware updates is a very welcoming feature in Intune. Where we have the opportunity to approve driver per driver and pause it when a driver update would fail. A good youtube Ask Me Anything session to watch is AMA: Windows updates in Intune: drivers, firmware, and Autopatch – YouTube
[…] Driver and firmware update via Intune […]