Microsoft announced that Defender for Endpoint will be available in two version from today. The two versions are P1 en P2. Where P1 is included in the Microsoft 365 E3 license an P2 is included in the E5 variant.
Defender for Endpoint P1 is focused on prevention/EPP including:
- Industry leading antimalware that is cloud-based with built-in AI that helps to stop ransomware, known and unknown malware, and other threats in their tracks.
- Attack surface reduction capabilities that harden the device, prevent zero days, and offer granular control over access and behaviors on the endpoint.
- Device based conditional access that offers an additional layer of data protection and breach prevention and enables a Zero Trust approach.
Differences between the two version

now we should onboard our devices.
Check in Endpoint security the connection status.
Go to https://endpoint.microsoft.com/
Click on Endpoint Security in de endpoint manager, under Setup click on Microsoft Defender for Endpoint
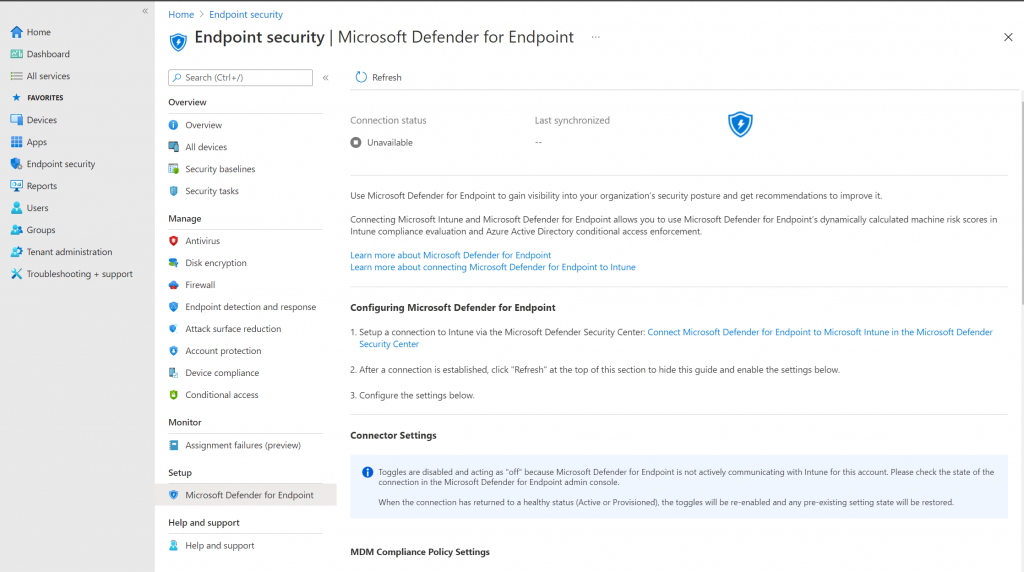
check if there is a connection available.
Connect Endpoint Manager to the Security Center
Connect the endpoint security to the Microsoft 365 Defender portal , go to https://securitycenter.windows.com/
Click on Settings , Advanced Features
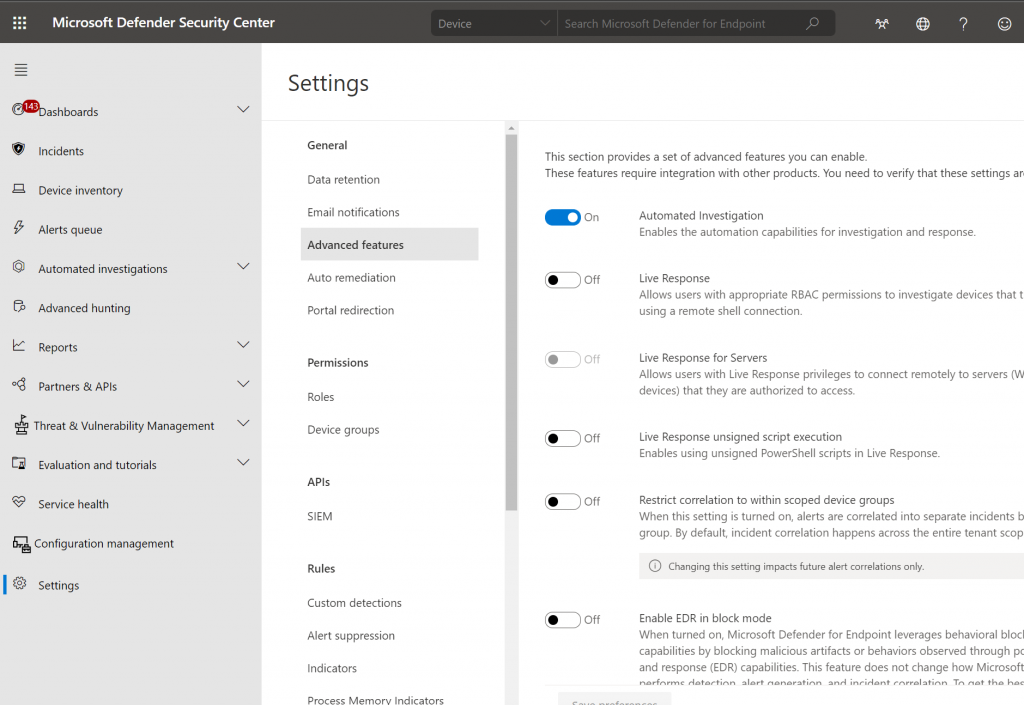
Scroll down to Microsoft Intune connection, set the slider to On

Click on Save Preferences.
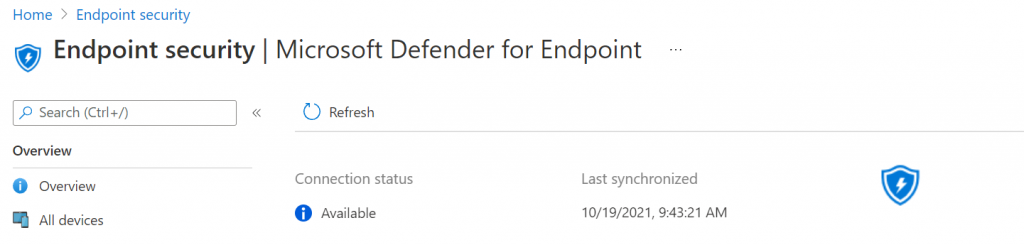
Now we have to go back to de endpoint manager to check the syncronization
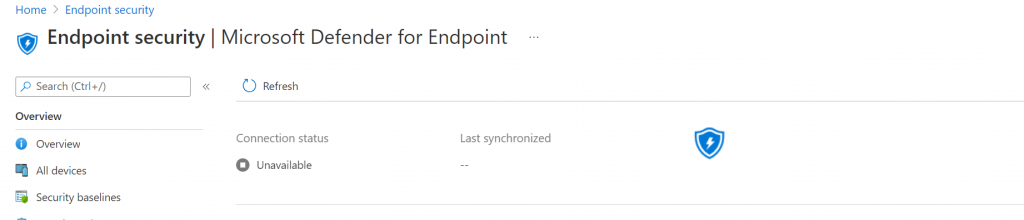
Click on Refresh
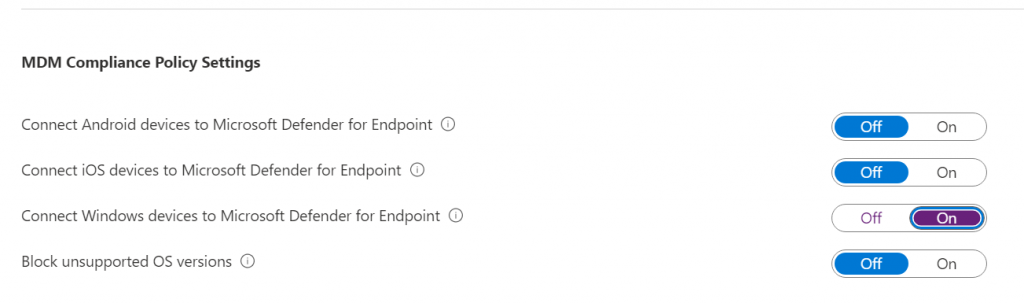
To use Defender for Endpoint with compliance policies, configure the following under MDM Compliance Policy Settings for the platforms you support:
- Set Connect Android devices to Microsoft Defender for Endpoint to On
- Set Connect iOS devices to Microsoft Defender for Endpoint to On
- Set Connect Windows devices to Microsoft Defender for Endpoint to On
For now we are only enroll Windows devices to compliance policies so turn the slider to on for Windows devices.
Click Save
Onboard Windows devices to Intune with a configuration profile
In Endpoint manager click on Endpoint Security and click on Endpoint detection and response
click on Create Policy
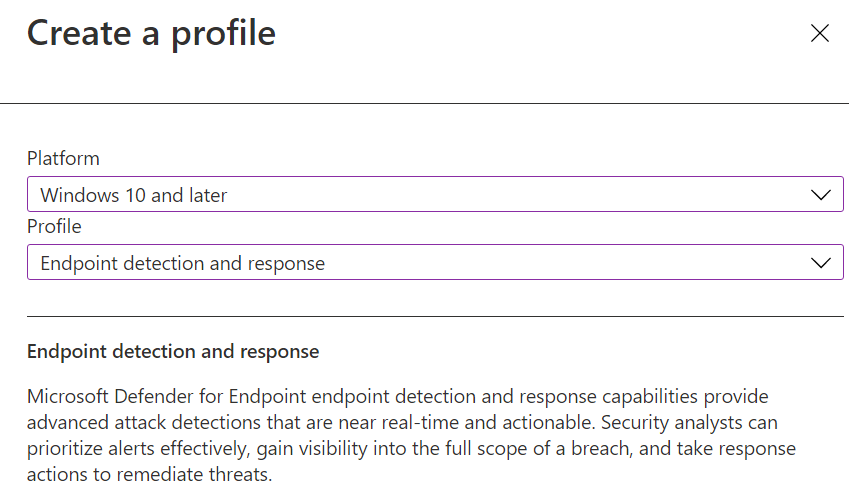
Select platform Windows 10 and later
Select Profile Endpoint detection and response
Enter a Name and Description and click Next, leave configuration settings as is for now click Next
Click Next on the scope tags page. Assign a group with you’re settings which devices you want to onboard, click Next and review the options and click on Create.
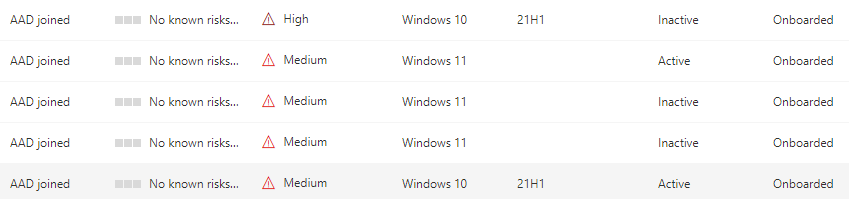
Now Check in the Security center if the device is onboarding.
Go to the security portal link
Click on Device inventory and have a look if the devices are onboarded an creating alerts and security recommendations