Microsoft released multiple administrative approvals (MAA in short) in public preview with one of their latest service releases. Which will give us the possibility to use Intune access policies, to require that a second administrative account is used to approve a change before the change is applied.
What is MAA
In a lot of circumstances, we have to make changes to our applications or scripts within Intune, internal setup, or customers. These changes have to be approved to be created in a production environment. Microsoft released the possibility to use multiple administrative approvals in Intune to let us create a policy or edit a policy with a business justification as part of the approval of the change request.
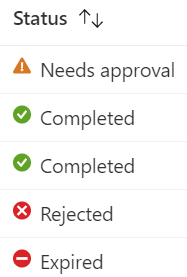
MAA needs access policies that protect specific configurations (Scripts and Apps for now) Access policies specify what is protected and which group of accounts are permitted to approve changes to those resources. After creating the access policy the one who is responsible for approving the change has to go to Multi Admin Administration > Received requests to see the change and respond to it with the following status conditions:
Needs approval – This request is pending action by an approver.
Approved – This request is being processed by Intune.
Completed – This request has been successfully applied.
Rejected – This request was rejected by an approver.
Canceled – This request was canceled by the admin who submitted it.
How to set up MAA.
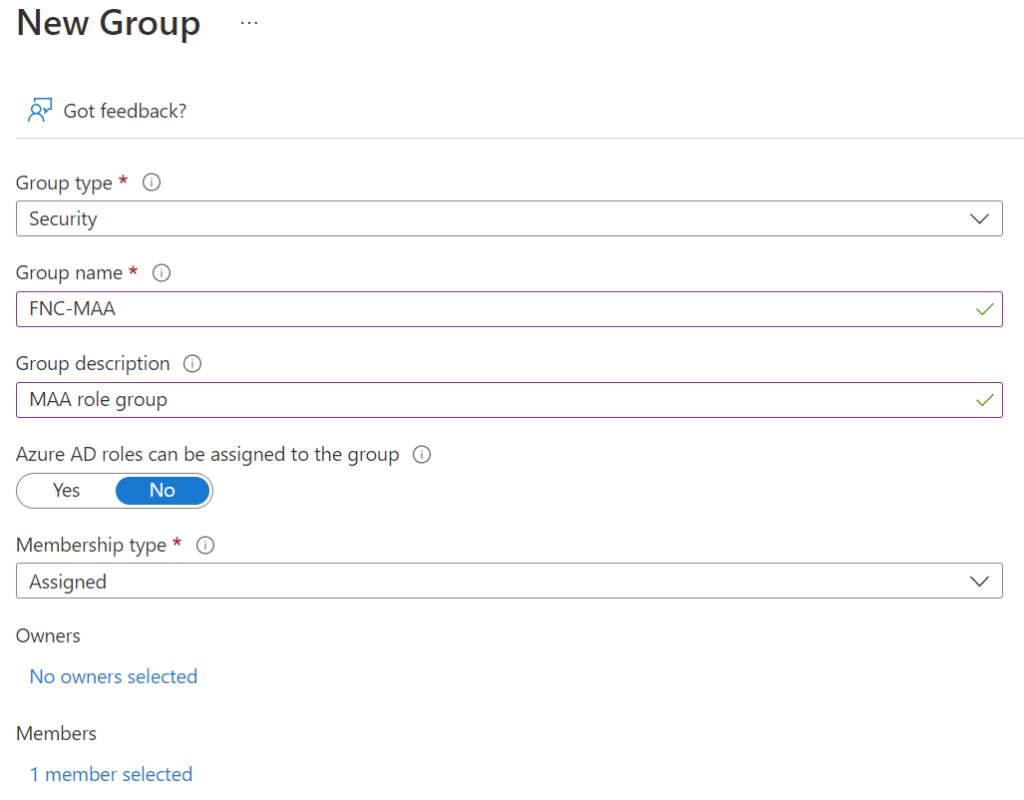
Now we have to set up MAA to get things going. Therefore the first step is to create a security group with the approver’s users as members. To this group, we are going to set the access policy.
Go to Intune | Groups | New Group, Choose security as group type, name the group and add members who will be responsible for the approval of changes.
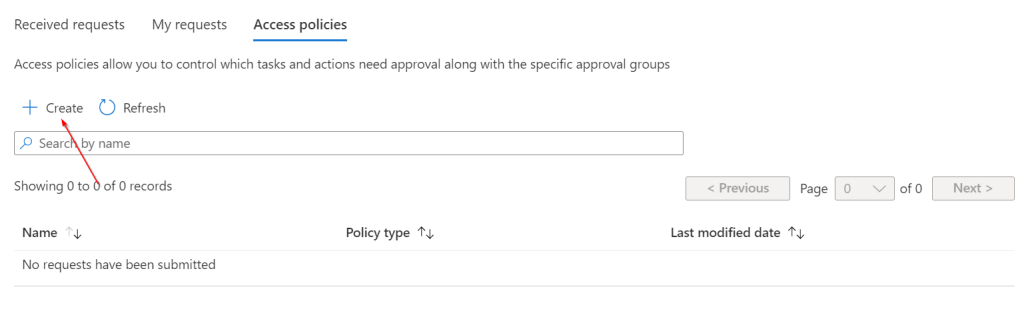
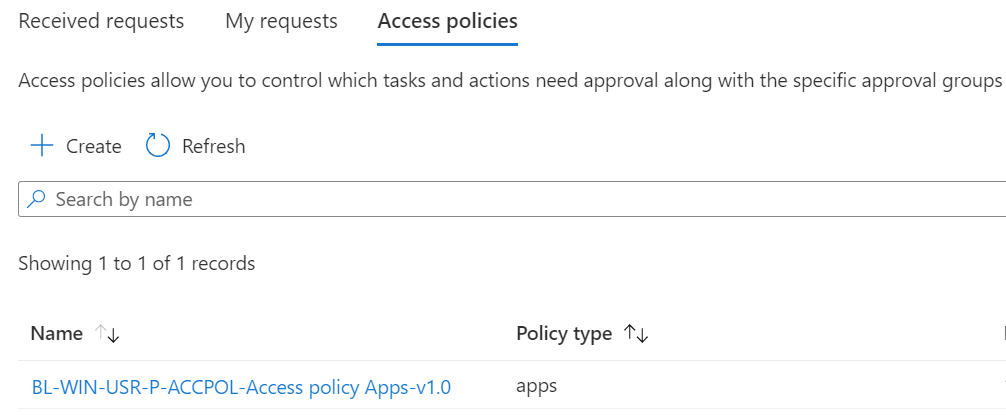
After creating the group we can create the access policy for that we need to go to
Tenant admin | Multi Admin Approval | Access policies
Click on + Create
Please give it a name and description and choose which profile you want to create the access policy for. For now, we can choose scripts and apps, hopefully, we can have more options when it goes out of public preview. We will choose apps as access policy.
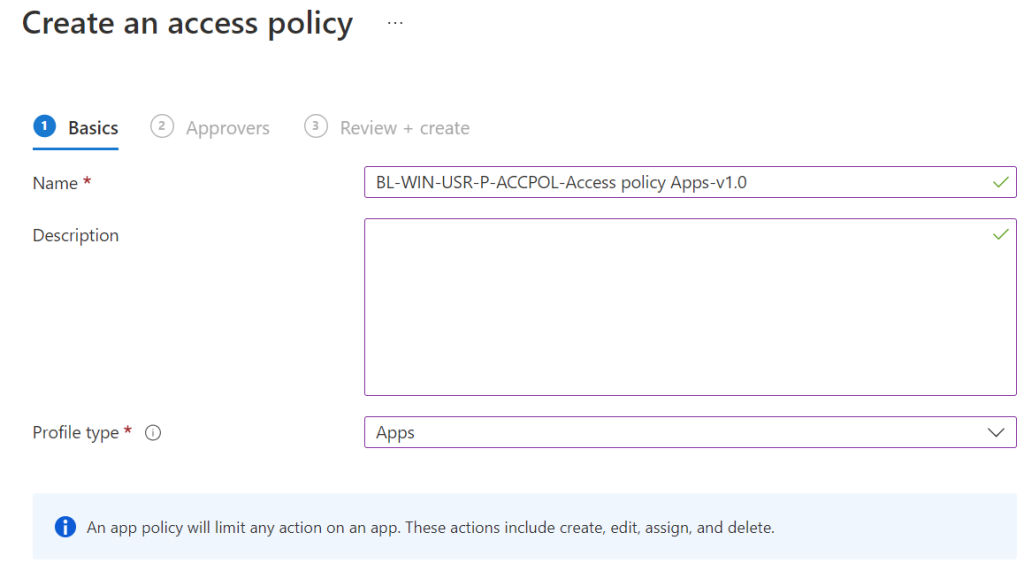
Click Next, assign the group with the approvers assigned and click Next and click Create
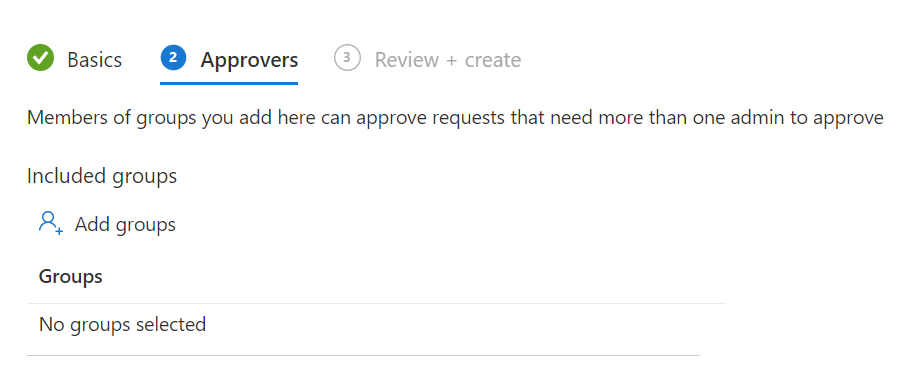
After completing it will look like the picture below
Demo
Now how will the process look like when created the access policy? Because we created an access policy for apps we can look for:
- Edit
- Create
- Modify
- Delete
- Assign
Admin experience
So we will create a new application with the new company store with an admin who can create applications.
Go to Windows | Windows apps and click on + Add, click on App type company store (new) click Select, and click on Search the Microsoft store app (new) we will add the company portal
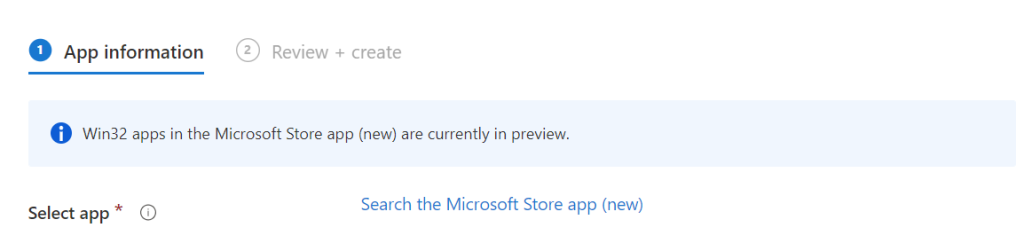
In the app creation a new field will appear
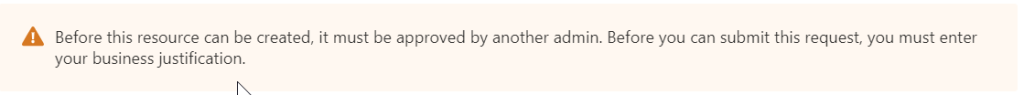
So we have to fill in a business justification, We fill in the “For our device setup we will add a company portal app for users helping them with compliancy issues or applications install Change number: 1743”
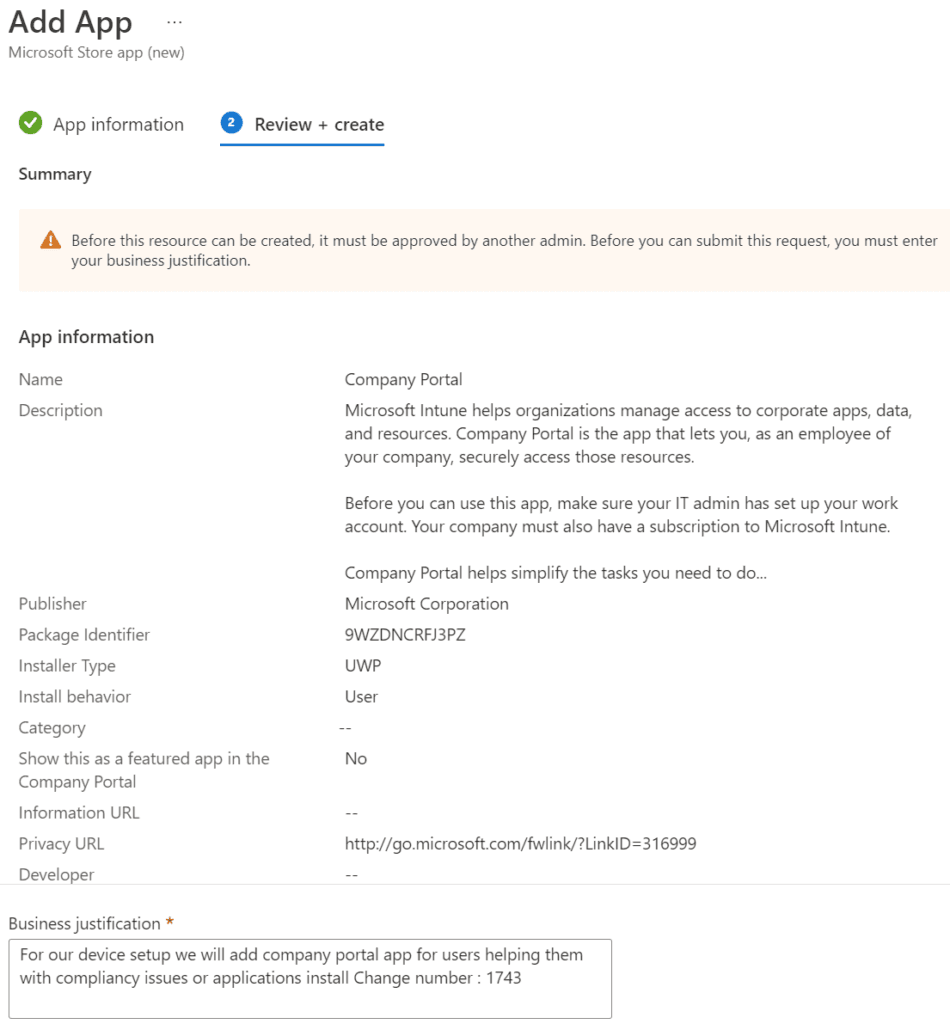
Click on Submit for approval. In the app itself, it will show the new message, which is clickable and will get us to the requested information and we can see all the information about the change.
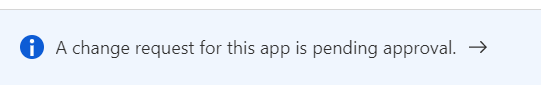
Approver experience
For the approver we have to go to Tenant admin | Multi Admin Approval | Received requests and we will see all requests made (all requests and updates remain there for 30 days)
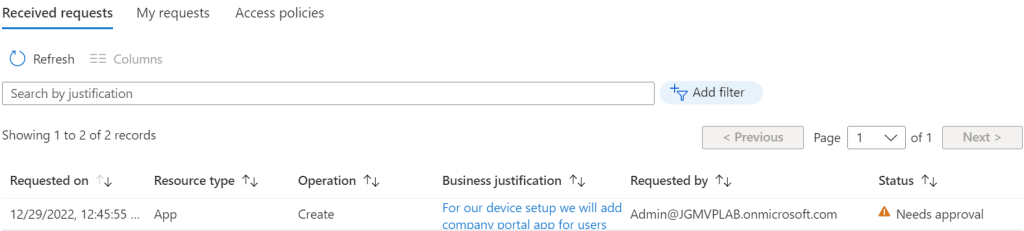
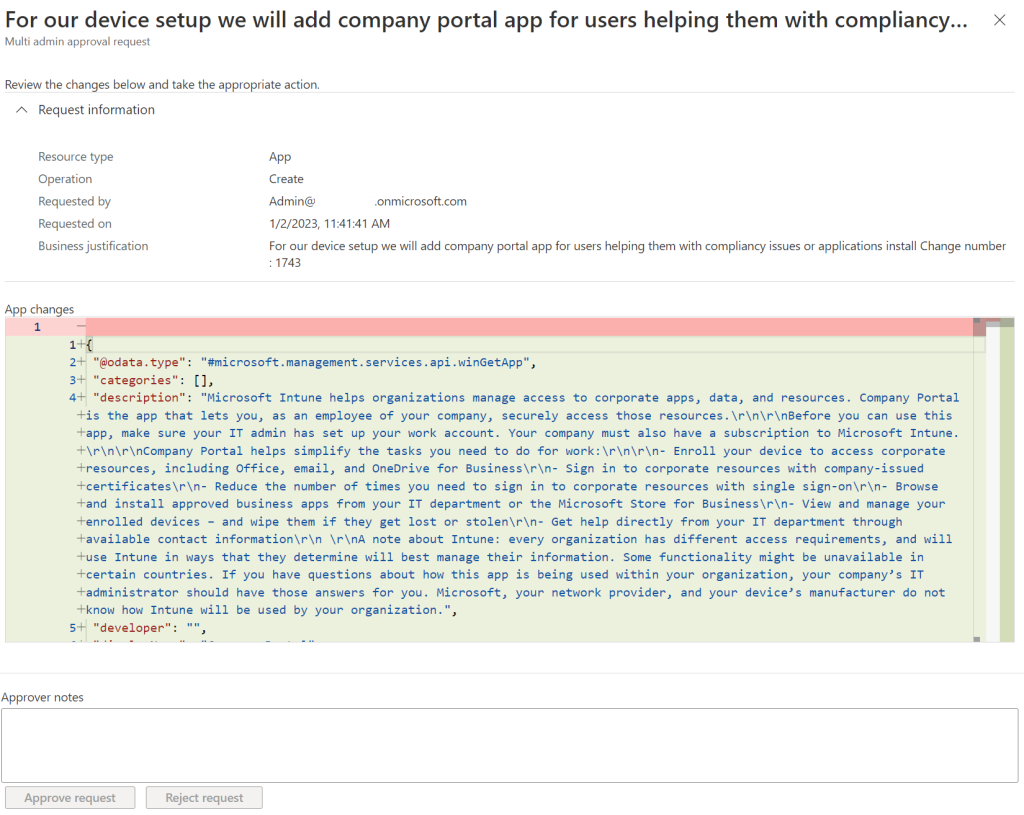
What we can see is the request made previously as an admin experience click on the business justification. the following view will appear where we can check which changes will be made.
Conclusion
MAA is a very nice feature in larger environments or with more customers we have to support. it can be beneficial with a 4 eye principle. Hoping Microsoft will add more features to MAA allowing more policies to be approved. Furthermore, Microsoft is going to use this as a security feature if an account is compromised it cannot create or change apps or scripts so this is always a welcoming feature

[…] Multiple Administrative approvals (MAA) Intune […]