Because we want to create the best user experience on our shared devices, we want to use Passwordless authentication with FIDO2. I just wrote a blog about how to create a self deploying shared device, on these device multiple users will sign-in and to give them the best logon experience we are enabling the possibility to logon with FIDO2 keys.
FIDO2 information
On the Microsoft site you will find some good information about FIDO2, but wanted to take piece of that information and place it here. The following process is used when a user signs in with a FIDO2 security key:
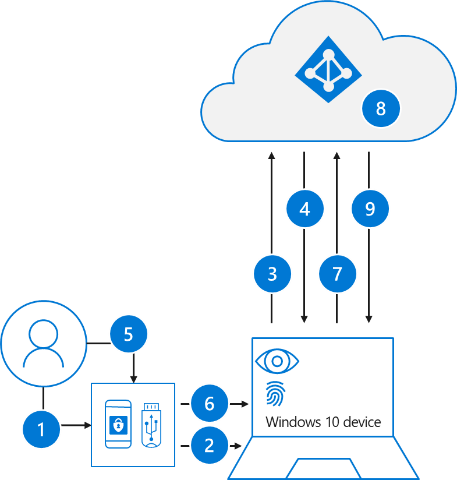
- The user plugs the FIDO2 security key into their computer.
- Windows detects the FIDO2 security key.
- Windows sends an authentication request.
- Azure AD sends back a nonce.
- The user completes their gesture to unlock the private key stored in the FIDO2 security key’s secure enclave.
- The FIDO2 security key signs the nonce with the private key.
- The primary refresh token (PRT) token request with signed nonce is sent to Azure AD.
- Azure AD verifies the signed nonce using the FIDO2 public key.
- Azure AD returns PRT to enable access to on-premises resources.
Enable FIDO2 as authentication method Admin experience
To enable FIDO2 as a authentication method on the devices and/or other sign-ins we have to do some changes as a admin.
Enable FIDO2 as passwordless authentication method in Azure
Configure your users in the authentication methods policy to enable passwordless authentication. Once configure the user can onboard the FIDO2 key. To enable it we have to make some changes in the Azure portal under security.
Go to https://portal.azure.com/ | Security | Authentication Methods
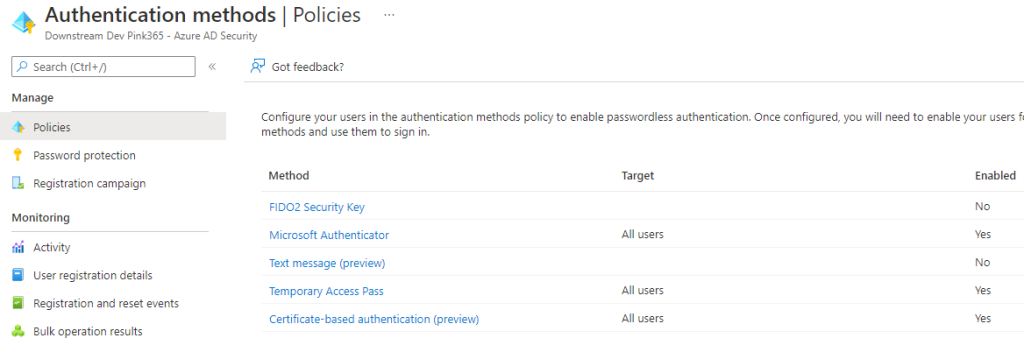
Click on method FIDO2 Security Key.
Now to enable it set the slider to Yes and leave it to All Users or if you want to selected users. I leave it on all users because its optional to use.
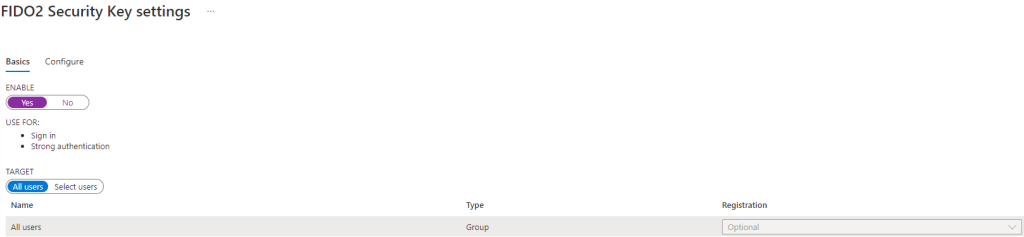
Click on Save
Create a Device policy to accept FIDO2 key’s in the logon screen
Go to Endpoint Manager | Devices | Configuration Profiles
Click on + Create Profile
We are going to create a Setting catalog for this (how to)
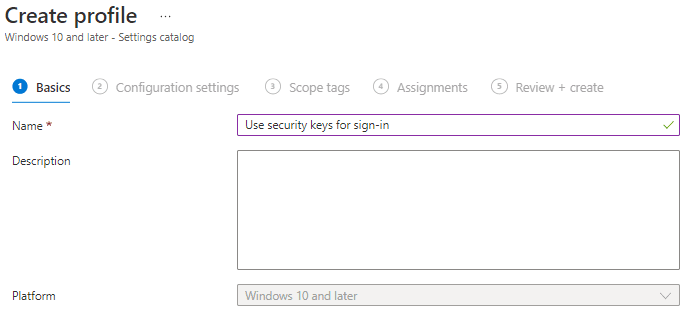
Click Next
Search for the Use Security Key For Signin setting and enable it.
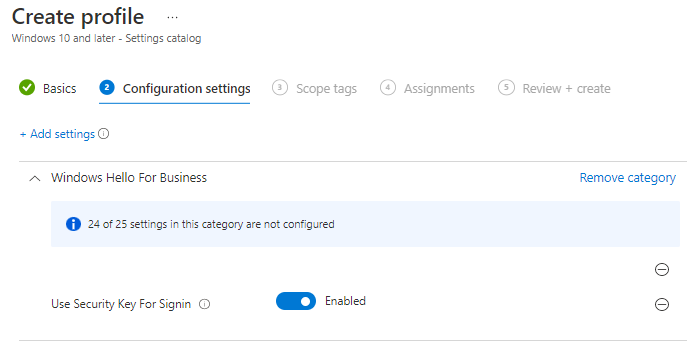
Assign the policy to a group of you’re liking in my case it will be set to dynamic shared device group. Now all settings to begin enrolling the FIDO2 keys are set and we can enroll an user with a key.
User Experience
A user needs to do some steps to enroll the FIDO2 key to their account in this case we assume the user already enrolled his account to MFA and knows his password otherwise you can use the new TAP possibility (maybe in a new blogpost)
In this blogpost I will be using the FIDO2 key of FEITIAN because of there biometric support, but we also use YubiKey or any other in the FIDO2 keys supported by Microsoft.

Provision the FIDO2 key to the user
The user has to sign in to My Sign-Ins | Security Info | Microsoft.com
Click on + Add sign-in method
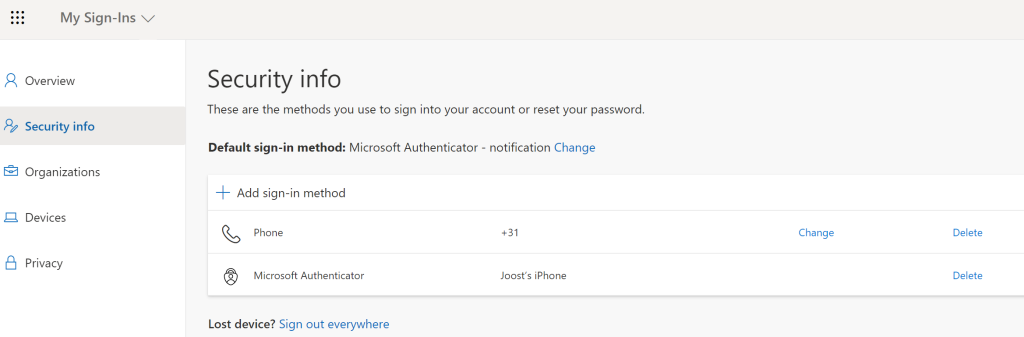
Add method by clicking on Security key and click Add
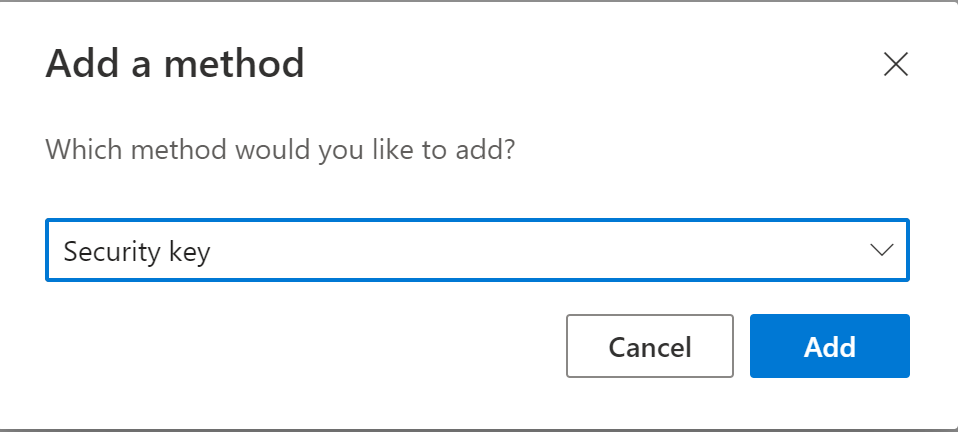
Choose the right device, in my case a USB device
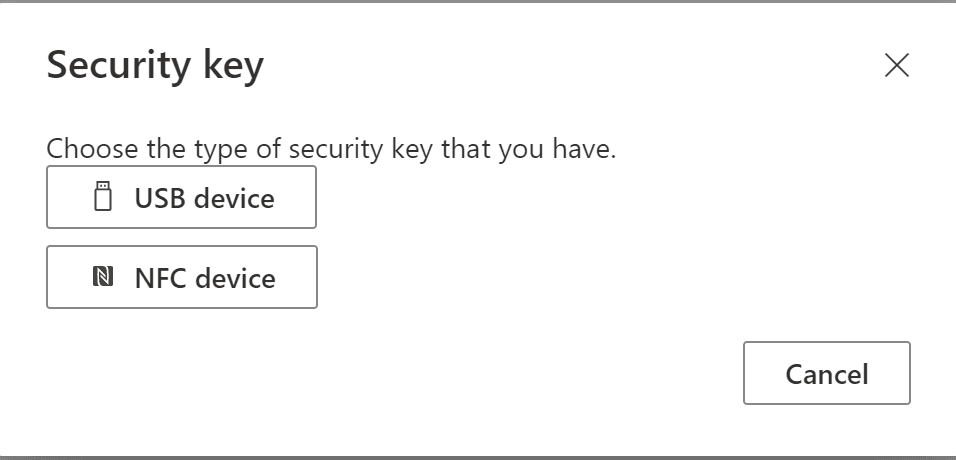
Place the USB device and click Next
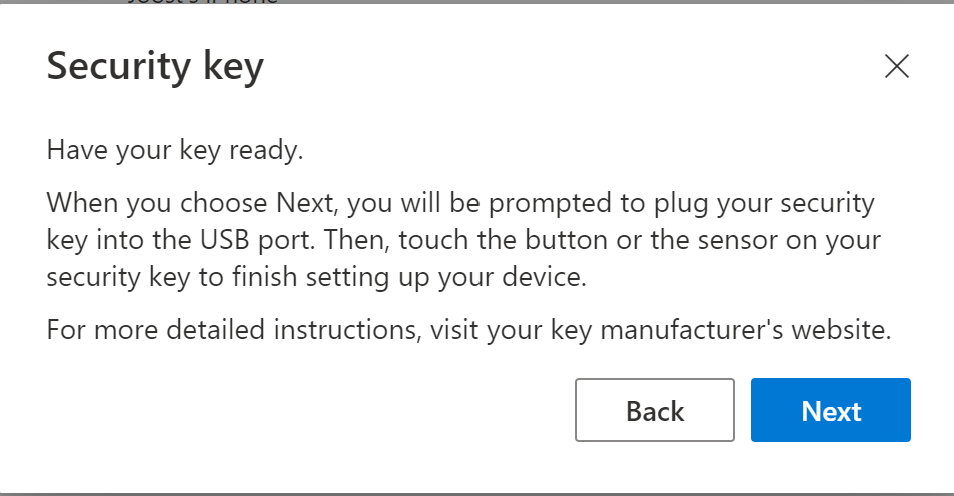
A redirection to a setup page will take place and will show the following in edge
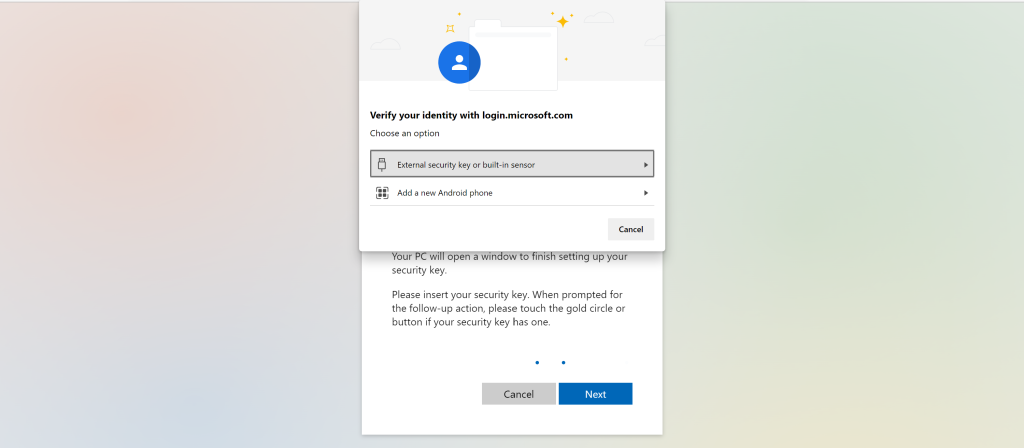
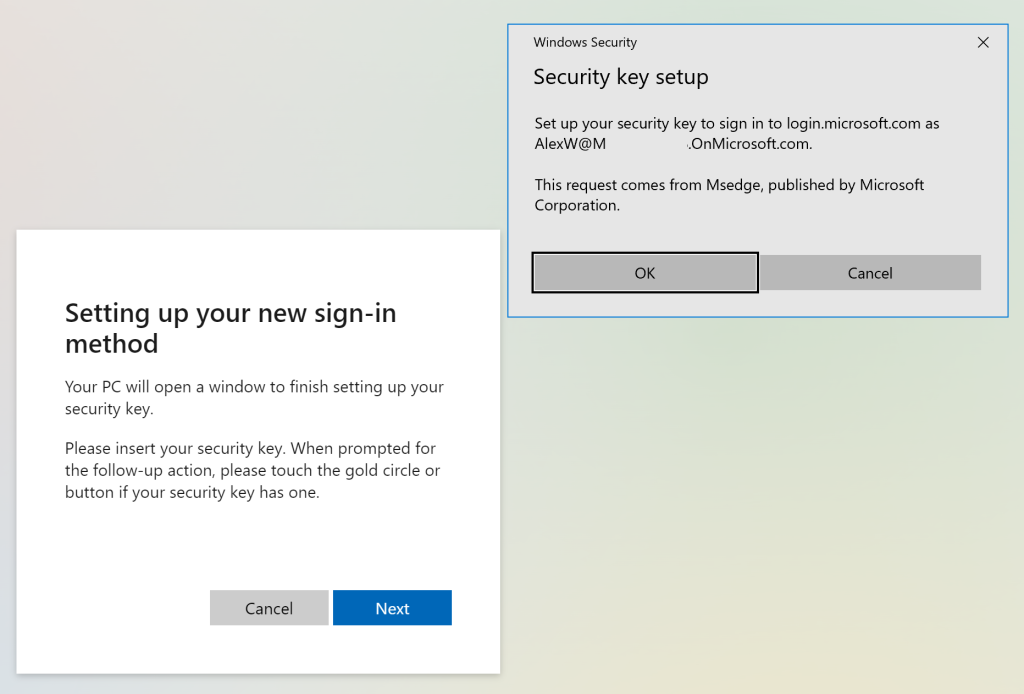
Click on External Security key or built-in sensor, Click on Next and OK
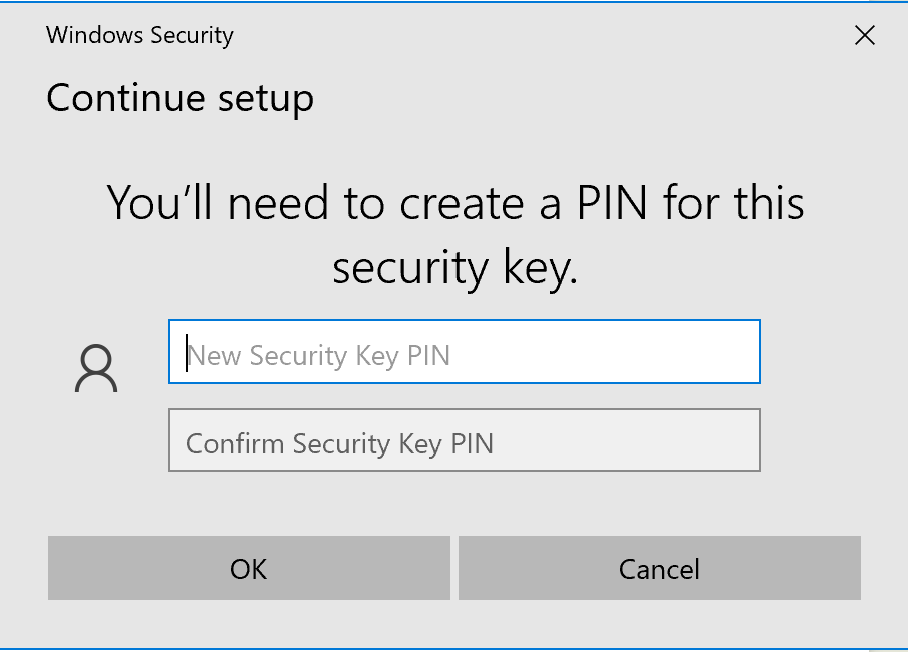
Create a Pin and click OK
The enrollment is now ready and the authentication method screen will have the the new security visible.
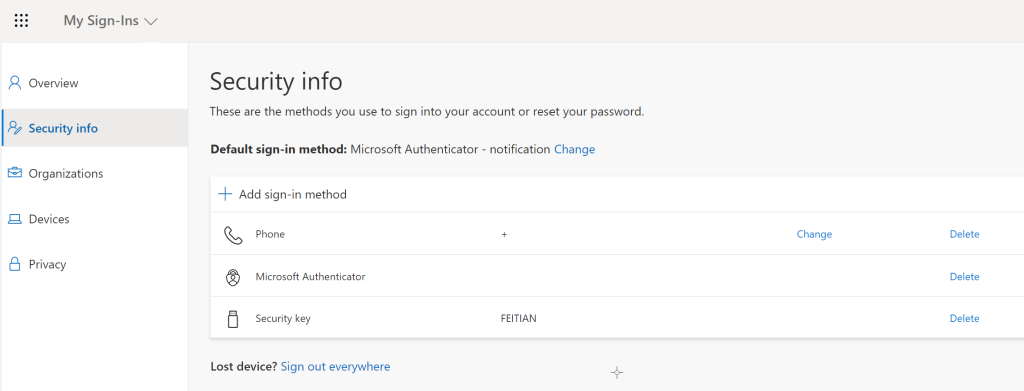
Sign-in user experience
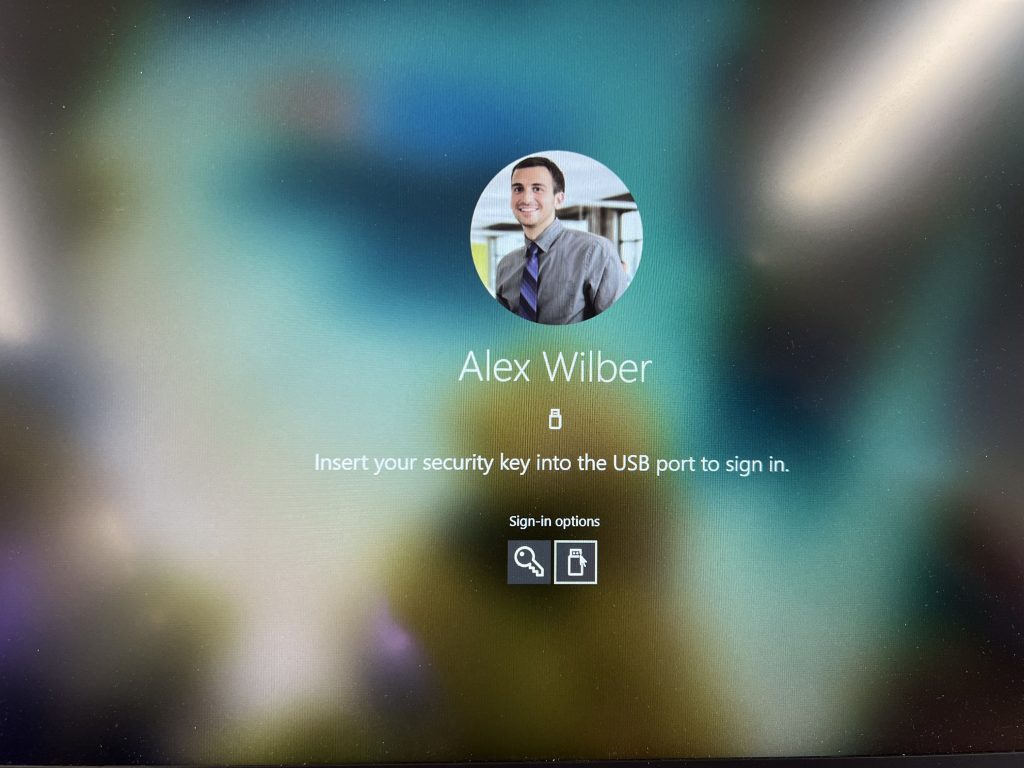
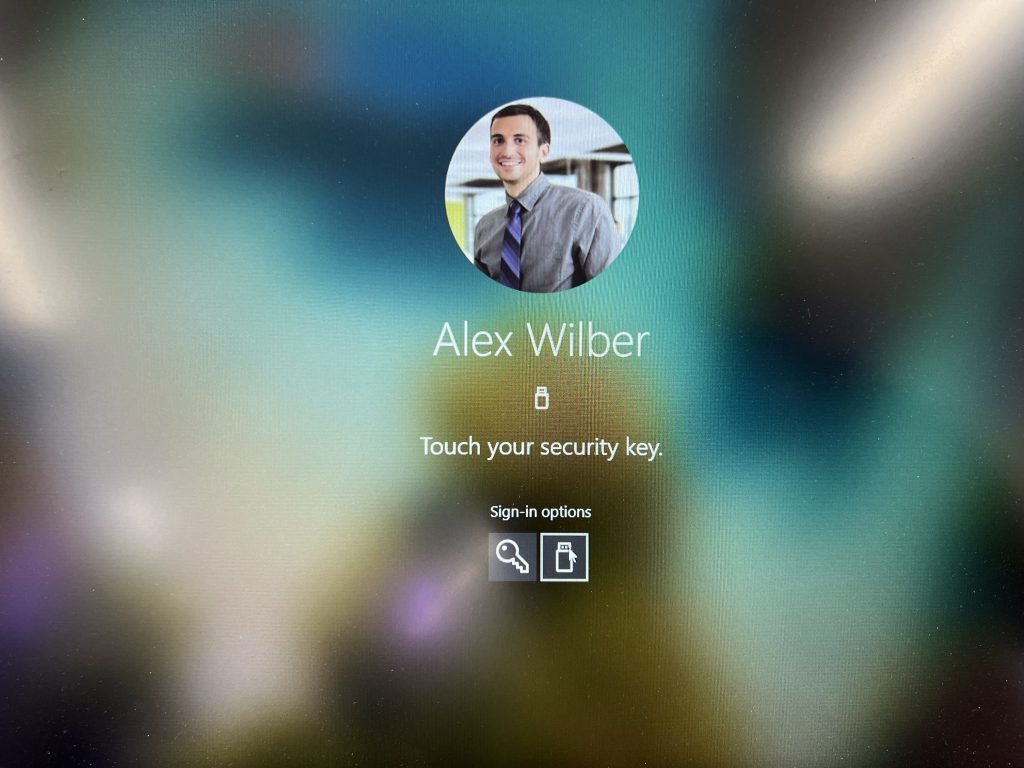
There are two possible ways to give the user there experience to logon windows:
- User types in pin and pushes button on the FIDO2 key, Windows logon will proceed
- User uses biometric of the FIDO2 key , Windows logon will proceed.
For the last type of experience the user has to do some additional steps adding the key to Windows hello or add FEITIAN his own software.
Overall experience of passwordless authentication is very nice and a welcoming feature.

[…] Passwordless authentication with FIDO2 […]