A lot of our customers are in the Care market, the care takers are working as multiple user on a device where they need to connect to several Web applications with SSO. The user can sign in to these shared device with a guest account. As they use the device, they only get access to features you allow. As the Intune administrator, you configure access, choose when accounts are deleted, control power management settings, and more for your shared Windows client devices.
To configure these shared multi-user devices I wanted to create a Self-deploying device and set the configuration of these shared devices with the Settings catalog
Requirements shared device
- Windows 10
- Windows 11
- TPM 2.0 Hardware
- Physical device ( Hyper-V virtual TPMs are not supported)
- Network requirements (link)
- No Enrollment restriction on all corporate devices (link)
Self-Deployment Configuration
Before we can create the multi-user shared device policy and the deployment profile we have to create a dynamic group with the shared device automatically as member.
Shared device dynamic group
We need to create a dynamic device group, I always like to use the Grouptag possibility for this. in this format I will use the Grouptag Shared. So the Dynamic membership rule will look like :
(device.devicePhysicalIds -any _ -eq “[OrderID]:Shared”)
How to create the Dynamic group in a step by step procedure I will link you this blog: Create a Dynamic Device group – Just about the Modern Workplace (joostgelijsteen.com)
Check enrollment restrictions
Because the enrollment is not using a user known in the tenant we have to check the enrollment restrictions.
Go to Enroll devices | Enrollment device platform restrictions
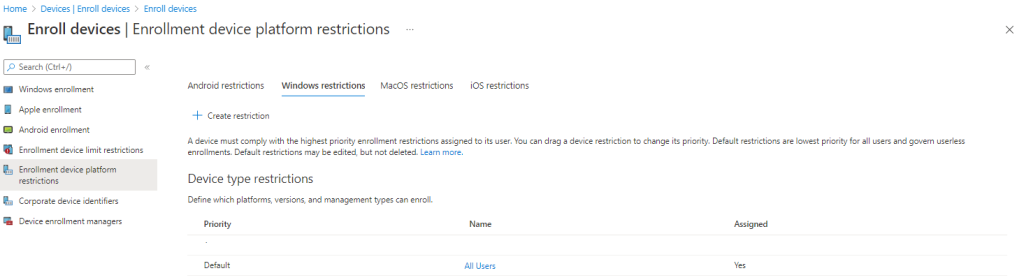
Click on All Users, properties
Check whether the Windows (MDM) for corporate devices is allowed.

Save this.
Create shared device self-deployment profile
To configure the device to be self-deployed we have to create a deployment profile with specific settings, in the following steps i will guide you through this.
Go to Devices, Enroll Devices, Deployment Profiles
Click on + Create profile and choose Windows PC
Fill in Name and click Next
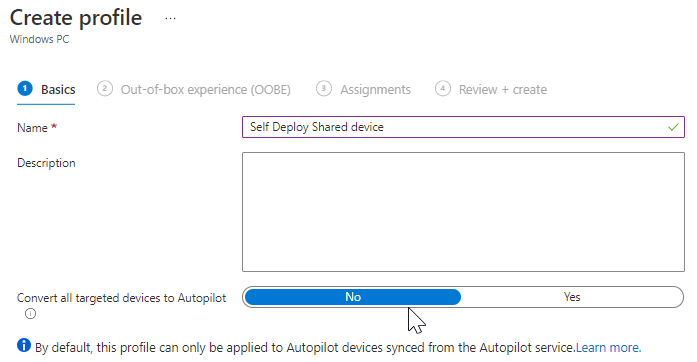
At the next step we need to tell the profile it will be Self-Deploying. At deployment mode choose Self-Deploying. Some configuration items will be greyed because off the Self-Deployment. I always like to us a naming convention therefore I will apply a device name template like S-%SERIAL%
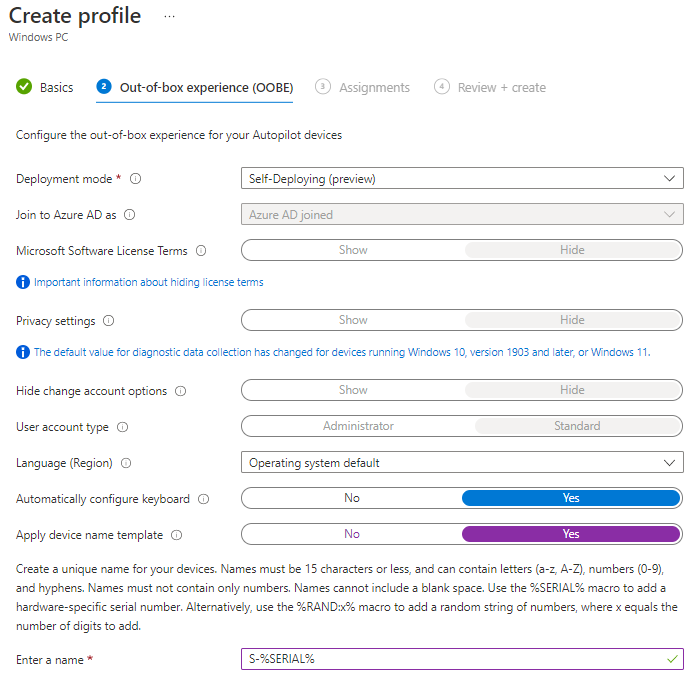
Click Next
Assign the policy created dynamic device group
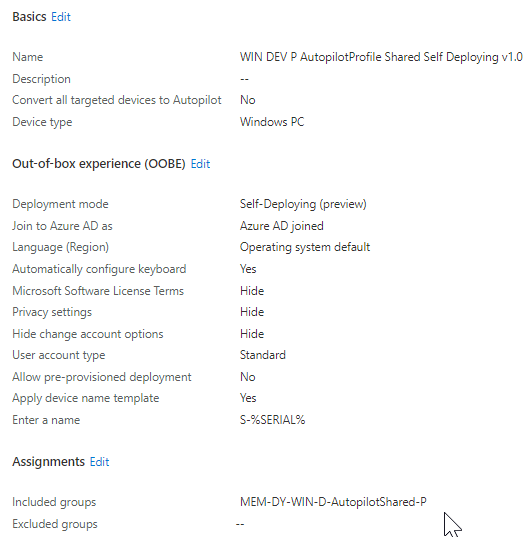
Create an Enrollment Status Page
Because we want to use specific settings for the ESP, we create a new one with specific settings and assign it to the dynamic device group.
Go to Devices, Enroll Devices, Enrollment Status Page
Click on + Create
Fill in Name and click Next
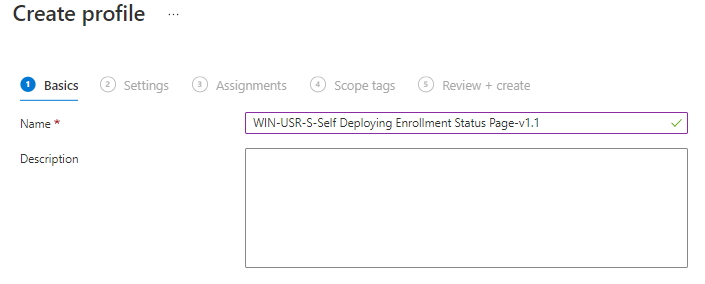
Click on Yes at the Show app and profile configuration progress
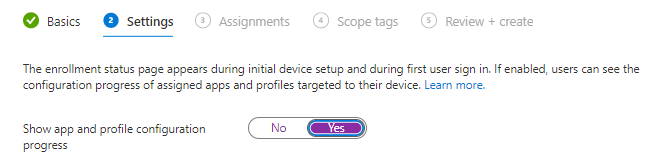
Fill in like below or in you’re liking and click Next
Assign it to the dynamic device group and click Next, Next and click on Create
Shared device configuration
Now we are ready with the self deployment configuration fase, we have to create a policy for the shared device. This has to be done because for several reasons but the biggest one is how is the device reacting to multiple users logging in to the device and leaf there profiles on the device. If no policy is set the device will be stuck with a full disk in no time.
I’m going to create these policy in the Settings Catalog and not use the separate policy for it.
The settings I will be using are in the screenshot below. how to create a settings catalog can be found here
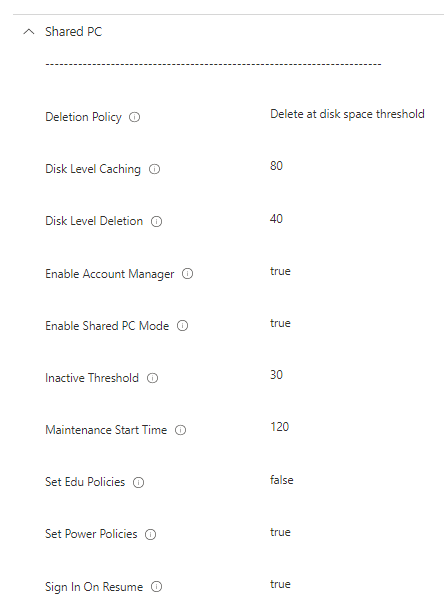
- Deletion Policy: Configures when accounts will be deleted.
- Disk Level Caching: Stop deleting accounts when available disk space reaches this threshold.
- Disk Level Deletion: Accounts will start being deleted when available disk space falls below this threshold, Accounts that have been inactive the longest will be deleted first.
- Enable Account Manager: Enable the account manager for shared PC mode
- Enable Shared PC Mode: configures a device to Shared PC mode.
- Inactive Threshold: Accounts will start being deleted when they have not been logged on during the specified period, given as number of days.
- Maintenance Start Time: Daily start time of maintenance hour. Given in minutes from midnight
- Set Edu Policies: disable this
- Set Power Policies: Set a list of power policy’s
- Sign In On Resume: Require signing in on waking up from sleep.
Experience Admin
- Once connected to a network WIFI or LAN, the Autopilot profile with the settings for the Self-Deploying device will be downloaded.
- WIFI and LAN will give the user a different experience:
- WIFI will go to manual steps for language, locale and last the keyboard.
- LAN will skip all the above steps and will proceed.
- In the Next step Windows will check if there any updates if so installed.
- Device will be joined to Azure AD and enrolled in Intune.
- The created ESP page will be displayed.
- Settings from Shared device setting catalog policy.
- The logon screen will show for the user to logon.

[…] Self-deploying shared device […]
[…] we want to use Passwordless authentication with FIDO2. I just wrote a blog about how to create a self deploying shared device, on these device multiple users will sign-in and to give them the best logon experience we are […]
[…] devices are a common devices at Care and Cure customers, multiple users have to logon to the shared devices to do there administration. What we see is that these users have to upload documents to […]