LAPS simplifies password rotation for local administrator accounts by generating unique, complex passwords. These passwords will be stored in the Azure Active Directory in the new Windows LAPS (Also can be stored in the Active Directory) It could be good to know how this rotation works and where to find events about it.
Password rotation policy
To let Windows LAPS rotate passwords, a policy must be created in Intune. In the following blog post, I made the policies step by step “LAPS around Intune“. But when the policy is set what happens on the device and what happens when we change the policy that’s something I will go into in this blog post.
Specific password rotation settings
Password age is a setting to configure the maximum password age of the managed local administrator account. When this policy is set the password of our LAPS administrator account will be rotated every time the age is reached we have set it to, If we set this policy to 30 days it will rotate if the password age becomes 30 days, the policy can have a value of 7 to 365 days.
A support engineer with correct rights can retrieve the LAPS password for a device from the catalog storing the LAPS password (AAD/AD). This password can be used to elevate or sign in as this user. We can use Post Authentication settings because we want to rotate the LAPS password after it has been used.
The Post Authentication action setting is used for what will happen with the LAPS password after authentication, this post-authentication will happen after the deadline expired. The hours can be set in the post-authentication reset delay which can be set from 0 to 24 hours.
Which policy change creates a password rotation
After some playing around with the LAPS policy I found out that some settings did not trigger a LAPS password to rotate. In some cases, it is good to know when the password rotates en when not.
When does a password change:
- Never previously updated the password (of course)
- Administrator Account Name
- A change in the RID of the customer-identified account
- A change in Policy Source
- If backing up passwords to Active Directory, these would also apply:
- Switching from a DSRM account to a local account (or vice-versa)
- Switching from password encryption to cleartext (or vice-versa)
- A change in the configured authorized encryptor target (ADPasswordEncryptionPrincipal)
When does a password not change:
- Changes to the PostAuthenticationResetDelay\Actions
- Changing the Password age setting
When creating a policy it is good to keep in mind when a password changes and when it doesn’t, We created a policy and placed it on our ring 1 users to start testing LAPS. In this testing phase, we went from 30 days of password age to 7 days but our password rotation wasn’t changed. it stayed on the 30 days. Even when looking into the event log where we can see what policy is sent to the device it is already on the right value.
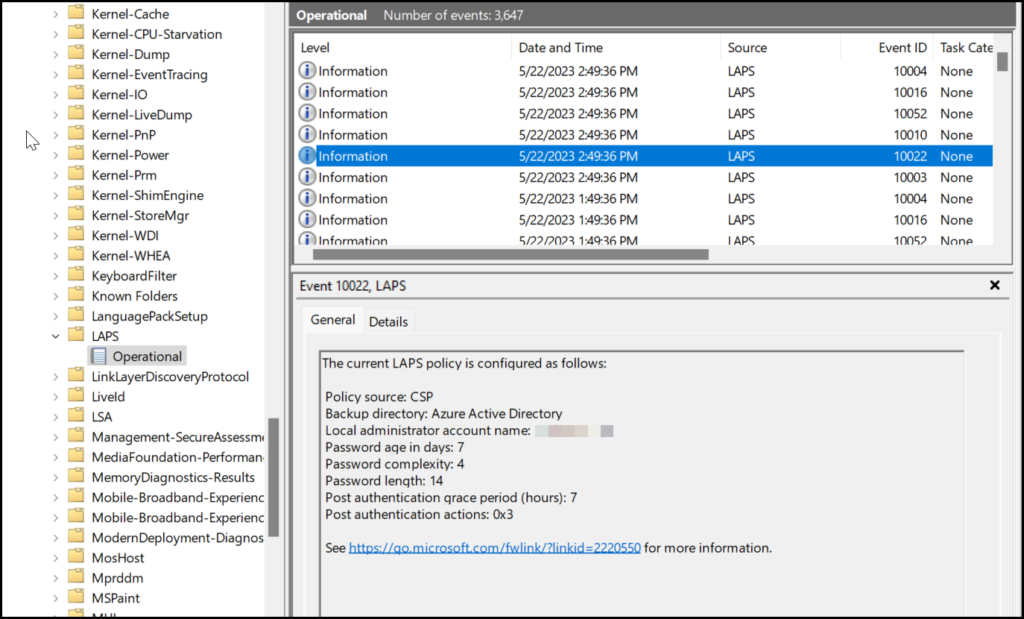
After 30 days it is going to rotate the password and the password age is set to 7 days. I have been chatting with one of the technicians at Microsoft who is responsible for LAPS and I was told this is by design, and that’s why I thought it was good to share this information to help out when creating the policy.
When I received feedback about what happens after authentication with the post-authentication actions and how we set the password age, I changed the password age back to 30 days.
What happens after an authentication deep dive
When doing authentication with the LAPS administrator account it is sometimes helpful to know what’s happening in the background. After authentication is done, something like elevating an installation with the LAPS administrator account the post-authentication settings will go to work.
Eventlog
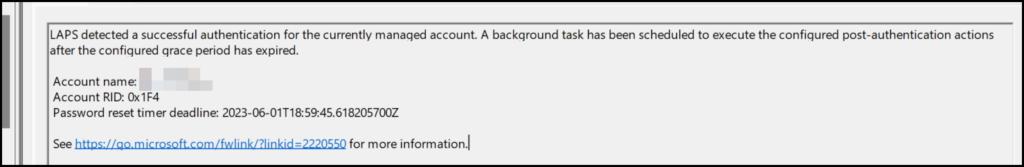
The first thing we will see is an eventid 10041 in the event log, which will tell us there was a successful authentication and when the reset time deadline is set.
Registry
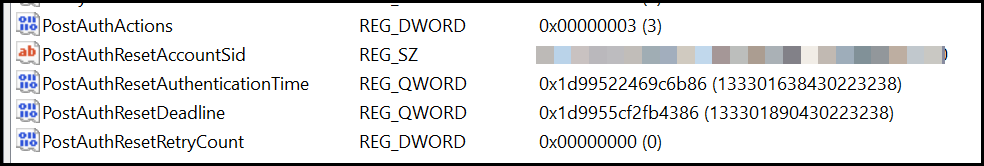
The second thing is in the registry under Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\LAPS\State, here we will find all PostAuth actions that will take place with the same reset timer deadline
Password Authentication Action (PAA)
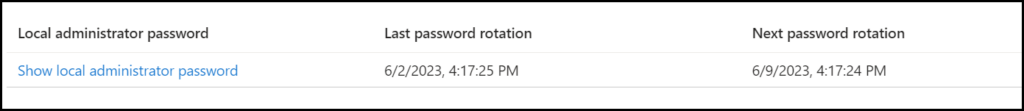
The password rotation will happen on the reset timer deadline and will retry that every hour if it somehow fails. After the reset time passed and the password is rotated in Azure which can be checked on the blade in Intune or Azure under devices
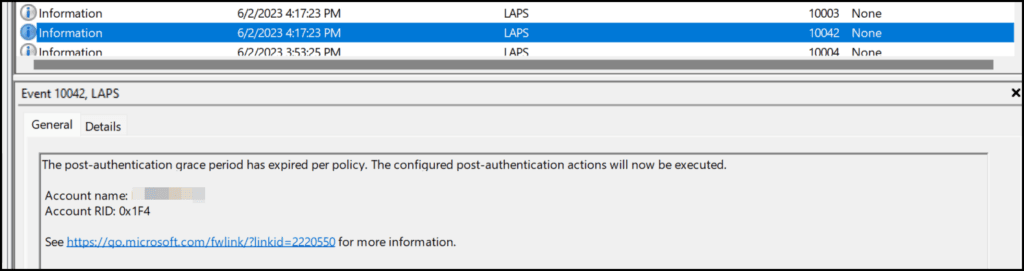
The Registry entries with the PostAuth will be deleted and an event is created with eventid 10042
Deeper diving
For a deeper dive into LAPS flow an PAA check this link of Rudy Ooms
